Difference between revisions of "Journal:Security and privacy in cloud-based eHealth systems"
Shawndouglas (talk | contribs) (Saving and adding more.) |
Shawndouglas (talk | contribs) m (Fixed citation issue) |
||
| (8 intermediate revisions by the same user not shown) | |||
| Line 6: | Line 6: | ||
|title_full = Security and privacy in cloud-based eHealth systems | |title_full = Security and privacy in cloud-based eHealth systems | ||
|journal = ''Symmetry'' | |journal = ''Symmetry'' | ||
|authors = Sivan, Remya; Zukarnain, Zuriati | |authors = Sivan, Remya; Zukarnain, Zuriati A. | ||
|affiliations = University Putra Malaysia | |affiliations = University Putra Malaysia | ||
|contact = Email: gs59108 at student dot upm dot edu dot my | |contact = Email: gs59108 at student dot upm dot edu dot my | ||
| Line 19: | Line 19: | ||
|download = [https://www.mdpi.com/2073-8994/13/5/742/pdf https://www.mdpi.com/2073-8994/13/5/742/pdf] (PDF) | |download = [https://www.mdpi.com/2073-8994/13/5/742/pdf https://www.mdpi.com/2073-8994/13/5/742/pdf] (PDF) | ||
}} | }} | ||
==Abstract== | ==Abstract== | ||
[[Cloud computing|Cloud-based]] healthcare computing has changed the face of healthcare in many ways. The main advantages of cloud computing in healthcare are scalability of the required service and the provision to upscale or downsize the data storge, particularly in conjunction with approaches to [[artificial intelligence]] (AI) and [[machine learning]]. This paper examines various research studies to explore the utilization of intelligent techniques in health systems and mainly focuses on the [[Information security|security]] and [[Information privacy|privacy]] issues in the current technologies. Despite the various benefits related to cloud computing applications for healthcare, there are different types of management, technology handling, security measures, and legal issues to be considered and addressed. The key focus of this paper is to address the increased demand for cloud computing and its definition, technologies widely used in healthcare, their problems and possibilities, and the way protection mechanisms are organized and prepared when the company chooses to implement the latest evolving service model. As such, we sought out current literature on different approaches and mechanisms used in [[eHealth]] to deal with security and privacy issues. Some of these approaches have strengths and weaknesses. After selecting original articles, a literature review was carried out, and we identified several models adopted in their solutions. We arrived at the reviewed articles after comparing the models used. | [[Cloud computing|Cloud-based]] healthcare computing has changed the face of healthcare in many ways. The main advantages of cloud computing in healthcare are scalability of the required service and the provision to upscale or downsize the data storge, particularly in conjunction with approaches to [[artificial intelligence]] (AI) and [[machine learning]]. This paper examines various research studies to explore the utilization of intelligent techniques in health systems and mainly focuses on the [[Information security|security]] and [[Information privacy|privacy]] issues in the current technologies. Despite the various benefits related to cloud computing applications for healthcare, there are different types of management, technology handling, security measures, and legal issues to be considered and addressed. The key focus of this paper is to address the increased demand for cloud computing and its definition, technologies widely used in healthcare, their problems and possibilities, and the way protection mechanisms are organized and prepared when the company chooses to implement the latest evolving service model. As such, we sought out current literature on different approaches and mechanisms used in [[eHealth]] to deal with security and privacy issues. Some of these approaches have strengths and weaknesses. After selecting original articles, a literature review was carried out, and we identified several models adopted in their solutions. We arrived at the reviewed articles after comparing the models used. | ||
| Line 31: | Line 26: | ||
==Introduction== | ==Introduction== | ||
Innovative changes in science, technology, and the broad understanding of our universe have permitted the evolution of practical, progressive answers to enhance the nature of human existence. Researchers considering these innovative developments have identified and assessed wellbeing data from various sources to acquire actionable information and address issues concerning human wellbeing, particularly in the realm of healthcare. In this manner, the advancement of incorporated medical care innovations—including technological innovations—has the likelihood to enhance efficiency and improve understanding of the results at each level of the medical care framework. Long-term care (LTC) facilities are a crucial a part of the healthcare industry, providing care to the fastest-growing group of the population. However, the adoption of [[electronic health record]]s (EHRs) in LTC facilities lags behind other areas of the health care industry.<ref name="KruseImpact17">{{cite journal |title=Impact of Electronic Health Records on Long-Term Care Facilities: Systematic Review |journal=JMIR Medical Informatics |author=Kruse, C.S.; Mileski, M.; Vijaykumar, A.G. et al. |volume=5 |issue=3 |at=e35 |year=2017 |doi=10.2196/medinform.7958 |pmid=28963091 |pmc=PMC5640822}}</ref> The advancement of new electronic health ([[eHealth]]) application frameworks can take care of specific issues pertinent to conventional medical care frameworks by means of powerful patient wellbeing controls, pervasive information access, distant patient checking, quick clinical intercession, and decentralized [[electronic medical record]]s. These frameworks can oversee wellbeing data and patient [[information]], upgrade personal satisfaction, increase coordinated effort, improve results, decrease expenses, and increase the general efficiency of electronic healthcare administrations.<ref name="ButphengSecur20">{{cite journal |title=Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review |journal=Symmetry |author=Butpheng, C.; Yeh, K.-H.; Xiong, H. |volume=12 |issue=7 |at=1191 |year=2020 |doi=10.3390/sym12071191}}</ref> For healthcare, EHRs are required to be shared among different healthcare organizations, medical drug manufacturers, pharmacists, medical insurance providers, researchers, and patients. This poses a significant challenge to keeping patients' sensitive data secure.<ref name="IsmailBlock20">{{cite journal |title=Blockchain Paradigm for Healthcare: Performance Evaluation |journal=Symmetry |author=Ismail, L.; Materwala, H. |volume=12 |issue=8 |at=1200 |year=2020 |doi=10.3390/sym12081200}}</ref> Eisenach highlights this in his depiction of eHealth as a tech industry that addresses the intersection of the internet, systems administration, and medical services, which has the potential to benefit the framework of clients and partners. The growing concept of eHealth involves the convergence of [[Health informatics|clinical informatics]], general human wellbeing, and the wellbeing and the use of a secure internet, which helps drive the overall advancement of new innovation to tackle profound issues, drive down expenses, and improve understanding.<ref name="MalluhiDecent20">{{cite journal |title=Decentralized Broadcast Encryption Schemes with Constant Size Ciphertext and Fast Decryption |journal=Symmetry |author=Malluhi, Q.; Tran, V.D.; Trinh, V.C |volume=12 |issue=6 |at=969 |year=2020 |doi=10.3390/sym12060969}}</ref> | Innovative changes in science, technology, and the broad understanding of our universe have permitted the evolution of practical, progressive answers to enhance the nature of human existence. Researchers considering these innovative developments have identified and assessed wellbeing data from various sources to acquire actionable information and address issues concerning human wellbeing, particularly in the realm of healthcare. In this manner, the advancement of incorporated medical care innovations—including technological innovations—has the likelihood to enhance efficiency and improve understanding of the results at each level of the medical care framework. Long-term care (LTC) facilities are a crucial a part of the healthcare industry, providing care to the fastest-growing group of the population. However, the adoption of [[electronic health record]]s (EHRs) in LTC facilities lags behind other areas of the health care industry.<ref name="KruseImpact17">{{cite journal |title=Impact of Electronic Health Records on Long-Term Care Facilities: Systematic Review |journal=JMIR Medical Informatics |author=Kruse, C.S.; Mileski, M.; Vijaykumar, A.G. et al. |volume=5 |issue=3 |at=e35 |year=2017 |doi=10.2196/medinform.7958 |pmid=28963091 |pmc=PMC5640822}}</ref> The advancement of new electronic health ([[eHealth]]) application frameworks can take care of specific issues pertinent to conventional medical care frameworks by means of powerful patient wellbeing controls, pervasive information access, distant patient checking, quick clinical intercession, and decentralized [[electronic medical record]]s (EMRs). These frameworks can oversee wellbeing data and patient [[information]], upgrade personal satisfaction, increase coordinated effort, improve results, decrease expenses, and increase the general efficiency of electronic healthcare administrations.<ref name="ButphengSecur20">{{cite journal |title=Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review |journal=Symmetry |author=Butpheng, C.; Yeh, K.-H.; Xiong, H. |volume=12 |issue=7 |at=1191 |year=2020 |doi=10.3390/sym12071191}}</ref> For healthcare, EHRs are required to be shared among different healthcare organizations, medical drug manufacturers, pharmacists, medical insurance providers, researchers, and patients. This poses a significant challenge to keeping patients' sensitive data secure.<ref name="IsmailBlock20">{{cite journal |title=Blockchain Paradigm for Healthcare: Performance Evaluation |journal=Symmetry |author=Ismail, L.; Materwala, H. |volume=12 |issue=8 |at=1200 |year=2020 |doi=10.3390/sym12081200}}</ref> Eisenach highlights this in his depiction of eHealth as a tech industry that addresses the intersection of the internet, systems administration, and medical services, which has the potential to benefit the framework of clients and partners. The growing concept of eHealth involves the convergence of [[Health informatics|clinical informatics]], general human wellbeing, and the wellbeing and the use of a secure internet, which helps drive the overall advancement of new innovation to tackle profound issues, drive down expenses, and improve understanding.<ref name="MalluhiDecent20">{{cite journal |title=Decentralized Broadcast Encryption Schemes with Constant Size Ciphertext and Fast Decryption |journal=Symmetry |author=Malluhi, Q.; Tran, V.D.; Trinh, V.C |volume=12 |issue=6 |at=969 |year=2020 |doi=10.3390/sym12060969}}</ref> | ||
Along these lines, models, gadgets, and frameworks associated with the [[internet of things]] (IoT) have become universal. Besides, the broad appropriation of IoT has harmonized with the improvement of interrelated, corresponding advances, for example, registering knowledge for medical care, business, industry, operational frameworks, etc. The efficient and safe usage of wellbeing data advancements, benefits, and all-encompassing eHealth frameworks requires exceedingly efficient and strong security frameworks to make such execution reasonable. The universality of IoT frameworks has driven the expansion of IoT innovation, remembering assorted designs for use by healthcare organizations. Connecting networks, gadgets, applications, and administration with IoT permits eHealth frameworks to share related data by utilizing the most recent IoT innovations.<ref name="HassenTowards20">{{cite journal |title=Towards a Secure Signature Scheme Based on Multimodal Biometric Technology: Application for IOT Blockchain Network |journal=Symmetry |author=Hassen, O.A.; Abdulhissein, A.A.; Darwish, S.M. et al. |volume=12 |issue=10 |at=1699 |year=2020 |doi=10.3390/sym12101699}}</ref> | Along these lines, models, gadgets, and frameworks associated with the [[internet of things]] (IoT) have become universal. Besides, the broad appropriation of IoT has harmonized with the improvement of interrelated, corresponding advances, for example, registering knowledge for medical care, business, industry, operational frameworks, etc. The efficient and safe usage of wellbeing data advancements, benefits, and all-encompassing eHealth frameworks requires exceedingly efficient and strong security frameworks to make such execution reasonable. The universality of IoT frameworks has driven the expansion of IoT innovation, remembering assorted designs for use by healthcare organizations. Connecting networks, gadgets, applications, and administration with IoT permits eHealth frameworks to share related data by utilizing the most recent IoT innovations.<ref name="HassenTowards20">{{cite journal |title=Towards a Secure Signature Scheme Based on Multimodal Biometric Technology: Application for IOT Blockchain Network |journal=Symmetry |author=Hassen, O.A.; Abdulhissein, A.A.; Darwish, S.M. et al. |volume=12 |issue=10 |at=1699 |year=2020 |doi=10.3390/sym12101699}}</ref> | ||
IoT and distributed computing are progressive innovations that supplement each other’s capacities when incorporated as flexible, versatile, and efficient tolerant medical service frameworks. The blend provides benefits, including simplicity of execution (contrasted with regular organizations), improved data security during correspondence, speedy access to records, and lower energy costs over customary modalities. Cloud-based IoT eHealth frameworks can significantly improve medical care benefits and advance persistent and efficient healthcare development. Within such frameworks, hidden IoT networks empower correspondence between clients, administrators, and workers, with clinical information being stored in the cloud. However, with new these improvements in distributed computing pushing healthcare beyond "business as usual," a variety of data storage and security issues are revealed, requiring consideration.<ref name="AbdulghaniAStudy19">{{cite journal |title=A Study on Security and Privacy Guidelines, Countermeasures, Threats: IoT Data at Rest Perspective |journal=Symmetry |author=Abdulghani, H.A.; Nijdam, N.A.; Collen, A. et al. |volume=11 |issue=6 |at=774 |year=2019 |doi=10.3390/sym11060774}}</ref> | IoT and distributed computing are progressive innovations that supplement each other’s capacities when incorporated as flexible, versatile, and efficient tolerant medical service frameworks. The blend provides benefits, including simplicity of execution (contrasted with regular organizations), improved data security during correspondence, speedy access to records, and lower energy costs over customary modalities. [[Cloud computing|Cloud-based]] IoT eHealth frameworks can significantly improve medical care benefits and advance persistent and efficient healthcare development. Within such frameworks, hidden IoT networks empower correspondence between clients, administrators, and workers, with clinical information being stored in the cloud. However, with new these improvements in distributed computing pushing healthcare beyond "business as usual," a variety of data storage and security issues are revealed, requiring consideration.<ref name="AbdulghaniAStudy19">{{cite journal |title=A Study on Security and Privacy Guidelines, Countermeasures, Threats: IoT Data at Rest Perspective |journal=Symmetry |author=Abdulghani, H.A.; Nijdam, N.A.; Collen, A. et al. |volume=11 |issue=6 |at=774 |year=2019 |doi=10.3390/sym11060774}}</ref> | ||
Distributed and cloud computing are innovations that have and continue to transform the healthcare industry. Distributed computing can help improve a healthcare organization's adaptability, savvy, finances, data processing ability, and secure data sharing and distribution.<ref name="KangTheDesign16">{{cite journal |title=The Design and Analysis of a Secure Personal Healthcare System Based on Certificates |journal=Symmetry |author=Kang, J.; Chung, H.; Lee, J. et al. |volume=8 |issue=11 |at=129 |year=2016 |doi=10.3390/sym8110129}}</ref> Cloud computing, when implemented well, should provide the ability to oversee applications and information, server accessibility, and end-used computing (EUC). Cloud computing should also ideally provide a complete, logical set of insights into a healthcare enterprise's infrastructure and end clients. By extension, cloud computing permits staff or workers to obtain and deal with their applications and information continuously on any gadget, from anywhere in the world with access to the internet.<ref name="GriebelAScoping15">{{cite journal |title=A scoping review of cloud computing in healthcare |journal=BMC Medical Informatics and Decision Making |author=Griebel, L.; Prokosch, H.-U.; Köpcke, F. et al. |volume=15 |at=17 |year=2015 |doi=10.1186/s12911-015-0145-7}}</ref> However, we recognize that a coordinated effort to move information to distributed systems and the cloud brings serious security and protection worries for healthcare providers. As such, they must endeavor to fully address the effectiveness of, security of, and versatility associated with the introduction of cloud-based eHealth to the healthcare enterprise. | Distributed and cloud computing are innovations that have and continue to transform the healthcare industry. Distributed computing can help improve a healthcare organization's adaptability, savvy, finances, data processing ability, and secure data sharing and distribution.<ref name="KangTheDesign16">{{cite journal |title=The Design and Analysis of a Secure Personal Healthcare System Based on Certificates |journal=Symmetry |author=Kang, J.; Chung, H.; Lee, J. et al. |volume=8 |issue=11 |at=129 |year=2016 |doi=10.3390/sym8110129}}</ref> Cloud computing, when implemented well, should provide the ability to oversee applications and information, server accessibility, and end-used computing (EUC). Cloud computing should also ideally provide a complete, logical set of insights into a healthcare enterprise's infrastructure and end clients. By extension, cloud computing permits staff or workers to obtain and deal with their applications and information continuously on any gadget, from anywhere in the world with access to the internet.<ref name="GriebelAScoping15">{{cite journal |title=A scoping review of cloud computing in healthcare |journal=BMC Medical Informatics and Decision Making |author=Griebel, L.; Prokosch, H.-U.; Köpcke, F. et al. |volume=15 |at=17 |year=2015 |doi=10.1186/s12911-015-0145-7}}</ref> However, we recognize that a coordinated effort to move information to distributed systems and the cloud brings serious security and protection worries for healthcare providers. As such, they must endeavor to fully address the effectiveness of, security of, and versatility associated with the introduction of cloud-based eHealth to the healthcare enterprise. | ||
| Line 44: | Line 39: | ||
The existing literature on eHealth security is difficult to survey. We originally identified and downloaded 40 papers from the ACM Digital Library, 57 articles from the IEEE Computer Society's Digital Library, and 43 from the IEEE Xplore library to provide a fair and calculable number of articles surveyed. Additional articles were also accessed from the specialized repositories of Springer, Elsevier, Science Direct, and MDPI. Few other papers from other sources were used as those sources were not as well-known and respected as from those cited. Of those papers analyzed, we identified 110 publications worthy of use in the face of conflicting evaluation models and methods used by many analysts. Due to the similarities found in the models obtained by some scientists, the analyzed papers were restricted to the momentum number. | The existing literature on eHealth security is difficult to survey. We originally identified and downloaded 40 papers from the ACM Digital Library, 57 articles from the IEEE Computer Society's Digital Library, and 43 from the IEEE Xplore library to provide a fair and calculable number of articles surveyed. Additional articles were also accessed from the specialized repositories of Springer, Elsevier, Science Direct, and MDPI. Few other papers from other sources were used as those sources were not as well-known and respected as from those cited. Of those papers analyzed, we identified 110 publications worthy of use in the face of conflicting evaluation models and methods used by many analysts. Due to the similarities found in the models obtained by some scientists, the analyzed papers were restricted to the momentum number. | ||
We then directly analyzed the papers, looking at and dissecting the strengths of each of the approaches obtained in seeking a solution to the security problem in eHealth. Through this process, we identified numerous shortcomings of the various proposed techniques, which eventually indicated a way forward to mitigate eHealth security incidents. Improving healthcare outcomes using eHealth is a developing area at the crossroads of clinical informatics, general human wellbeing, and patient health data that is securely communicated and enhanced through the internet and related technologies.<ref name="VenčkauskasAModel16">{{cite journal |title=A Model-Driven Framework to Develop Personalized Health Monitoring |journal=Symmetry |author=Venčkauskas, A.; Štuikys, V.; Toldinas, J. et al. |volume=8 |issue=7 |at=65 |year=2016 |doi=10.3390/sym8070065}}</ref> <ref name="KhanAnIoT20">{{cite journal |title=An IoT Framework for Heart Disease Prediction Based on MDCNN Classifier |journal=IEEE Access |author=Khan, M.A. |volume=8 |pages=34717–27 |year=2020 |doi=10.1109/ACCESS.2020.2974687}}</ref><ref name="YangImplem20">{{cite journal |title=Implementation of Lightweight eHealth Applications on a Low-Power Embedded Processor |journal=IEEE Access |author=Yang, M.; Hara-Azumi, Y. |volume=8 |pages=121724–32 |year=2020 |doi=10.1109/ACCESS.2020.3006901}}</ref><ref name="GuoADecrypt20">{{cite journal |title=A Decryptable Attribute-Based Keyword Search Scheme on eHealth Cloud in Internet of Things Platforms |journal=IEEE Access |author=Guo, L.; Li, Z.; Yau, W.-C. et al. |volume=8 |pages=26107–18 |year=2020 |doi=10.1109/ACCESS.2020.2971088}}</ref> The use of eHealth in the healthcare setting represents not olny a specialized turn of events from a more traditional approach, but also a perspective, a demeanor, and a duty for coordinated, national efforts to enhance patient care through the use of information and communication technologies locally, territorially, and internationally.<ref name="EdemacuPrivacy19">{{cite journal |title=Privacy Provision in Collaborative Ehealth With Attribute-Based Encryption: Survey, Challenges and Future Directions |journal=IEEE Access |author=Edemacu, K.; Park, H.K.; Jang, B. et al. |volume=7 |pages=89614—89636 |year=2019 |doi=10.1109/ACCESS.2019.2925390}}</ref> | We then directly analyzed the papers, looking at and dissecting the strengths of each of the approaches obtained in seeking a solution to the security problem in eHealth. Through this process, we identified numerous shortcomings of the various proposed techniques, which eventually indicated a way forward to mitigate eHealth security incidents. Improving healthcare outcomes using eHealth is a developing area at the crossroads of clinical informatics, general human wellbeing, and patient health data that is securely communicated and enhanced through the internet and related technologies.<ref name="VenčkauskasAModel16">{{cite journal |title=A Model-Driven Framework to Develop Personalized Health Monitoring |journal=Symmetry |author=Venčkauskas, A.; Štuikys, V.; Toldinas, J. et al. |volume=8 |issue=7 |at=65 |year=2016 |doi=10.3390/sym8070065}}</ref><ref name="KhanAnIoT20">{{cite journal |title=An IoT Framework for Heart Disease Prediction Based on MDCNN Classifier |journal=IEEE Access |author=Khan, M.A. |volume=8 |pages=34717–27 |year=2020 |doi=10.1109/ACCESS.2020.2974687}}</ref><ref name="YangImplem20">{{cite journal |title=Implementation of Lightweight eHealth Applications on a Low-Power Embedded Processor |journal=IEEE Access |author=Yang, M.; Hara-Azumi, Y. |volume=8 |pages=121724–32 |year=2020 |doi=10.1109/ACCESS.2020.3006901}}</ref><ref name="GuoADecrypt20">{{cite journal |title=A Decryptable Attribute-Based Keyword Search Scheme on eHealth Cloud in Internet of Things Platforms |journal=IEEE Access |author=Guo, L.; Li, Z.; Yau, W.-C. et al. |volume=8 |pages=26107–18 |year=2020 |doi=10.1109/ACCESS.2020.2971088}}</ref> The use of eHealth in the healthcare setting represents not olny a specialized turn of events from a more traditional approach, but also a perspective, a demeanor, and a duty for coordinated, national efforts to enhance patient care through the use of information and communication technologies locally, territorially, and internationally.<ref name="EdemacuPrivacy19">{{cite journal |title=Privacy Provision in Collaborative Ehealth With Attribute-Based Encryption: Survey, Challenges and Future Directions |journal=IEEE Access |author=Edemacu, K.; Park, H.K.; Jang, B. et al. |volume=7 |pages=89614—89636 |year=2019 |doi=10.1109/ACCESS.2019.2925390}}</ref> | ||
===Research strategy=== | ===Research strategy=== | ||
| Line 58: | Line 53: | ||
==Cloud computing and the state of the art== | ==Cloud computing and the state of the art== | ||
Cloud computing—a set of internet-based, always-on computing services provisioned on an as-needed or continuous basis—is organized into three different service models: [[infrastructure as a service]] (IaaS), [[platform as a service]] (PaaS), and [[software as a service]] (SaaS). | |||
IaaS is a cloud service model that delivers computing resources, networking, and storage to consumers. It enables end users to upscale or downsize resources on an as-needed basis, reducing the need for compute upscaling, up-front capital expenditures, and unnecessary infrastructure.<ref name="MaRevoc19">{{cite journal |title=Revocable Attribute-Based Encryption Scheme With Efficient Deduplication for Ehealth Systems |journal=IEEE Access |author=Ma, H.; Xie, Y.; Wang, J. et al. |volume=7 |pages=89205–17 |year=2019 |doi=10.1109/ACCESS.2019.2926627}}</ref><ref name="CaizaReusable19">{{cite journal |title=Reusable Elements for the Systematic Design of Privacy-Friendly Information Systems: A Mapping Study |journal=IEEE Access |author=Caiza, J.C.; Martin, Y.-S.; Guamán, D.S. et al. |volume=7 |pages=66512–35 |year=2019 |doi=10.1109/ACCESS.2019.2918003}}</ref> PaaS is a cloud service model that provides an application development and deployment environment to comsumers. PaaS platforms handle the complexity around operating systems and servers and leaves application developers more time to focus their business requirements to the software they are developing. SaaS is a cloud service model that delivers software to customers with relative ease; all you need is an internet connection and a browser. This service model requires the cloud vendor to manage most of their technical issues, meaning customers need not heavily lean on their in-house IT expertise for hosting and maintaining the software. | |||
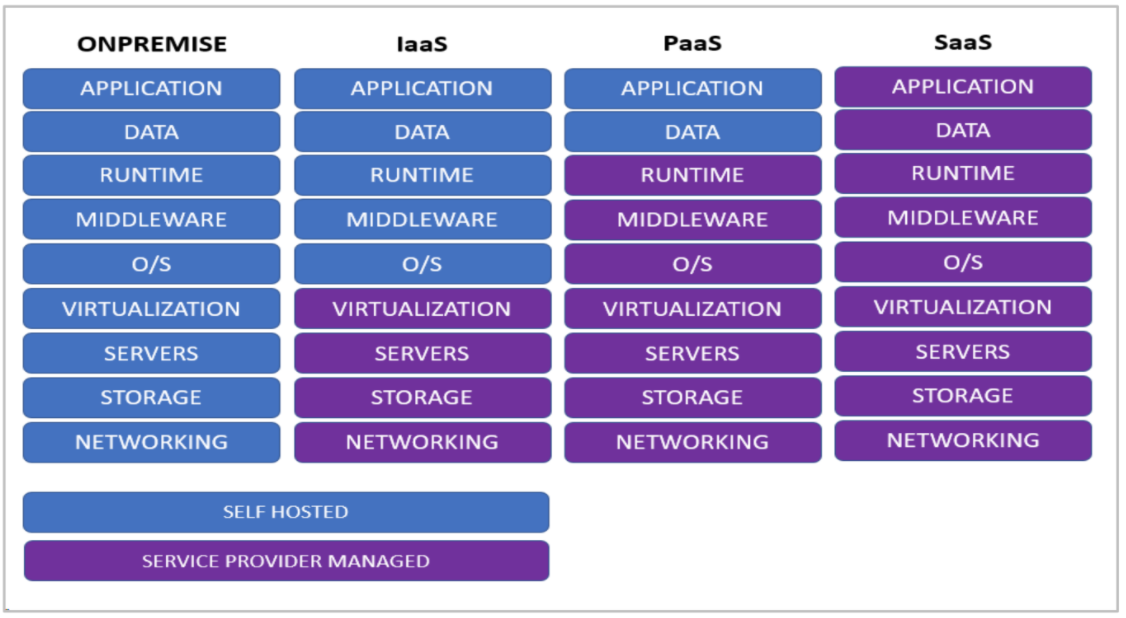
Figure 1 take a high-level look at these cloud infastructures, as compared with on-premises offerings. Light blue indicates customer responsibility, and dark blue indicates cloud provider responsibility. | |||
[[File:Fig1 Sivan Symmetry21 13-5.png|800px]] | |||
{{clear}} | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"| <blockquote>'''Figure 1.''' Cloud service models and responsibilities, compared with on-premises systems. Light blue indicates customer responsibility, and dark blue indicates cloud provider responsibility.</blockquote> | |||
|- | |||
|} | |||
|} | |||
The eHealth system is a newly developed space that contains electronic processes and communications. EHRs and EMRs act as a compilation of digital patient health data, containing demographic information, diagrams, patient medical information, patient medications, [[hospital]] or clinic reports, radiology photographs, billing information, and other sensitive patient information. Cloud computing offers a cost-effective way of effectively storing, processing, and updating that type of data with efficiency and quality.<ref name="ChentharaSecurity19">{{cite journal |title=Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing |journal=IEEE Access |author=Chenthara, S.; Ahmed, K.; Wang, H. et al. |volume=7 |pages=74361–82 |year=2019 |doi=10.1109/ACCESS.2019.2919982}}</ref> Cloud computing also offers the advantage of access to hosted services from multiple locations around the world with by multiple users. | |||
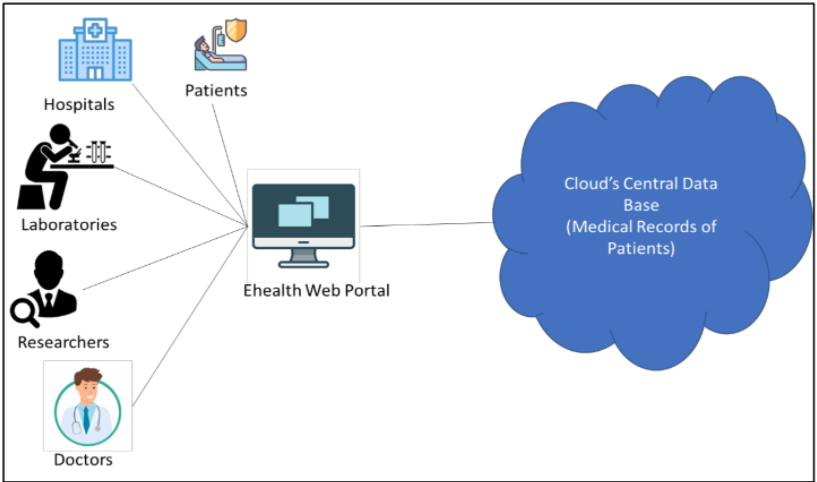
Separately, eHealth systems promise faster, robust, and sought-after access to medical records, fewer medical regulations, and improved health care quality, though they also should ideally maintain patient privacy, prevent improper authorization, and prevent misuse of sensitive patient data. When using these eHealth systems in the cloud, maintaining security and privacy are especially critical when sharing or accessing patient data. An overview of e-health structures in the scope of cloud computing is shown in Figure 2. | |||
[[File:Fig2 Sivan Symmetry21 13-5.png|700px]] | |||
{{clear}} | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| border="0" cellpadding="5" cellspacing="0" width="700px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"| <blockquote>'''Figure 2.''' eHealth architecture in the scope of cloud computing.</blockquote> | |||
|- | |||
|} | |||
|} | |||
There are a number of deployment models for cloud computing, including public cloud, private cloud, and hybrid cloud. Public cloud deployments make resources available to private and public users via the internet as an ongoing or on-demand service, allowing clients to pay only for what they use or subscribe to. Instead of purchasing a physical server and networking equipment, a public cloud customer can purchase a virtual server and network that can be accessed from anywhere. The public cloud relies on a customized environment to provide corporate infrastructure expansion, allowing the company to host certain aspects of its infrastructure and services on virtual and identifiable third-party servers. Public cloud service providers have unique capabilities, and they offer excellent types of services and price models. However, companies considering migration to public cloud must carefully consider their options when it comes to choosing a provider, especially if there is a possibility of service being preemptively terminated in a long-term contract. Careful planning can help reduce the cost of monthly payments for cloud services, but organizations with unplanned or unexpected usage requirements may find it difficult to avoid spending large sums on public cloud services.<ref name="RazaqueSurv19">{{cite journal |title=Survey: Cybersecurity Vulnerabilities, Attacks and Solutions in the Medical Domain |journal=IEEE Access |author=Razaque, A.; Amsaad, F.; Khan, M.J. et al. |volume=7 |pages=168774–97 |year=2019 |doi=10.1109/ACCESS.2019.2950849}}</ref> | |||
Private clouds are cloud installations used exclusively by a single organization and its authorized users, usually in the form of a single network or datacenter that provides services hosted to a specific group of people. Private clouds offer easy access and more control over security for the organizations using them. Although a private cloud is less expensive than using a public cloud, the cost is not easily measured. The development or growth of private cloud infrastructure will require the purchase of additional equipment. Similarly, when the need for a private cloud decreases, expensive resources and equipment are inevitably misused.<ref name="KimMPPDS19">{{cite journal |title=MPPDS: Multilevel Privacy-Preserving Data Sharing in a Collaborative eHealth System |journal=IEEE Access |author=Kim, J.W.; Edemacy, K.; Jang, B. |volume=7 |pages=109910–23 |year=2019 |doi=10.1109/ACCESS.2019.2933542}}</ref><ref name="BourasDistrib20">{{cite journal |title=Distributed Ledger Technology for eHealth Identity Privacy: State of The Art and Future Perspective |journal=Sensors |author=Bouras, M.A.; Lu, Q.; Zhang, F.; et al. |volume=20 |issue=2 |at=483 |year=2020 |doi=10.3390/s20020483 |pmid=31952172 |pmc=PMC7013398}}</ref> | |||
A hybrid cloud infrastructure is a combination of two or more integrated public and private clouds. In hybrid cloud infrastructure, the organization provides and manages their own resources within the private data center while also using additional outsourced public and private services—such as VMware that works in tandem with Fortinet Networks—to provide a hybrid cloud infrastructure that allows for increased organizational security on private and remote servers while the public cloud is largely secured by the cloud provider. Hybrid cloud is usually an excellent deal for those debating between a public cloud and a private cloud. The hybrid cloud environment allows organizations to take advantage of both types of cloud platforms and choose which cloud will provide the specific data needs. For example, the hybrid cloud provides another way to store sensitive company data and information, allowing the organization to maintain sensitive security configurations in the private cloud while conducting other business activities in the public cloud.<ref name="SeolPrivacy18">{{cite journal |title=Privacy-Preserving Attribute-Based Access Control Model for XML-Based Electronic Health Record System |journal=IEEE Access |author=Seol, K.; Kim, Y.-G.; Lee, E. et al. |volume=6 |pages=9114—28 |year=2018 |doi=10.1109/ACCESS.2018.2800288}}</ref><ref name="ZhuAnEff18">{{cite journal |title=An Efficient and Privacy-Preserving Biometric Identification Scheme in Cloud Computing |journal=IEEE Access |author=Zhu, L.; Zhang, C.; Xu, C. et al. |volume=6 |pages=19025–33 |year=2018 |doi=10.1109/ACCESS.2018.2819166}}</ref> | |||
===Advantages of cloud-based eHealth systems=== | |||
The more a healthcare center integrates system data and information via a global computer network such as the internet, the more global risk that is placed into the information network due to the expansion of breachable information access points. The need to access sensitive patient information should be limited to authorized users and protected from illegal users who may misuse that information for a variety of purposes. Identity-based [[encryption]] (IBE) has so far proven to be one of the best security solutions to protect eHealth record data.<ref name="QadirIEEE17">{{cite journal |title=IEEE Access Special Section Editorial: Health Informatics for the Developing World |journal=IEEE Access |author=Qadir, J.; Mujeeb-U-Rahman, M.; Rehmani, M.H. et al. |volume=5 |pages=27818–23 |year=2017 |doi=10.1109/ACCESS.2017.2783118}}</ref><ref name="YehASecure16">{{cite journal |title=A Secure IoT-Based Healthcare System With Body Sensor Networks |journal=IEEE Access |author=Yeh, K.-H. |volume=4 |pages=10288–99 |year=2016 |doi=10.1109/ACCESS.2016.2638038}}</ref> The encryption algorithm deals with problems found in common cryptographic techniques using any thread as a public key. The system can further enhance the security of health records by adding authentication procedures to three connected servers. In this system, communication between three servers uses IBE to encrypt data, such that each server can perform the encryption and decryption process during the data exchange. Only servers with authorized IDs can access and extract health record data. Currently, test results show performance relative to the speed of the algorithm used in the system.<ref name="IslamTheInter15">{{cite journal |title=The Internet of Things for Health Care: A Comprehensive Survey |journal=IEEE Access |author=Islam, S.M.R.; Kwak, D.; Kabir, H. et al. |volume=3 |pages=678–708 |year=2015 |doi=10.1109/ACCESS.2015.2437951}}</ref><ref name="TahirASystem20">{{cite journal |title=A Systematic Review on Cloud Storage Mechanisms Concerning e-Healthcare Systems |journal=Sensors |author=Tahir, A.; Chen, F.; Khan, H.U. et al. |volume=20 |issue=18 |at=5392 |year=2020 |doi=10.3390/s20185392 |pmid=32967094 |pmc=PMC7570508}}</ref> | |||
As discussed here, and by Vilela ''et al.''<ref name="VilelaLooking20">{{cite journal |title=Looking at Fog Computing for E-Health through the Lens of Deployment Challenges and Applications |journal=Sensors |author=Vilela, P.H.; Rodrigues, J.J.P.C.; Righi, R.da R. et al. |volume=20 |issue=9 |at=2553 |year=2020 |doi=10.3390/s20092553}}</ref>, cloud storage involves sending data over the internet to a remote cloud data center for storage. Cloud storage is delivered according to demand, capacity, and cost requirements, giving the customer control over how they invest in and manage their data storage infrastructure. This model has the advantage of lending speed, scale, and durability to an organization's eHealth data management. | |||
Running eHealth systems in the cloud has additional advantages as well, including: | |||
* Ease of access using a web browser and integrated single sign-on (SSO) | |||
* No requirement for a virtual private network (VPN) to access other sites or networks | |||
* Simplified data management and on-demand scalability | |||
* No overhead cost to maintain the physical infrastructure | |||
* No hardware-related post-warranty charges for the physical infrastructure | |||
* Little to no additional power consumption | |||
Mechanism commonly used in the cloud also lend to eHealth systems. For example, one of the major schemes in healthcare systems is attribute-based encryption for data. Encryption provides high-class access control for every user, as well as revocation, scalability, dynamic user management, and traceability. Users have high-grade login access, which can be integrated with two-factor authentication (2FA) as well as one-time passwords (OTP) for every access. Similarly, users’ access can be revoked from a centralized management console at any point in time by the administrator. The most important advantage is that every access can be recorded and traced, and clipping can be implemented for each session.<ref name="HaquePrivacy20">{{cite journal |title=Privacy-Preserving K-Nearest Neighbors Training over Blockchain-Based Encrypted Health Data |journal=Electronics |author=Haque, R.U.; Hasan, A.S.M.T.; Jiang, Q. et al. |volume=9 |issue=12 |at=2096 |year=2020 |doi=10.3390/electronics9122096}}</ref> Privileged access management (PAM) is another technology which can be used if there are many subsystems that a user needs to access at a single point in time. | |||
Another cloud-based scheme for eHealth systems involves robust and secure access control, which resolves single-point performance bottleneck problems. This solves the majority of security access control issues, as the certificate needs to be trusted and issued from a certified hosting platform. The main disadvantage, however, is that there is no process or mechanism for attribute revocation. | |||
==Security issues of cloud-based eHealth systems== | |||
Despite the advantages cloud computing brings to eHealth, it still has its own security challenges which emerge from time to time due to inadequate compliance with proper security protocols and best practices. Some of those challenges include<ref name="StamatellisAPriv20">{{cite journal |title=A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric |journal=Sensors |author=Stamatellis, C.; Papadopoulos, P.; Pitropakis, N. et al. |volume=20 |issue=22 |at=6587 |year=2020 |doi=10.3390/s20226587 |pmid=33218022 |pmc=PMC7698751}}</ref><ref name="YaqoobSecurity19">{{cite journal |title=Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review |journal=IEEE Communications Surveys & Tutorials |author=Yaqoob, T.; Abbas, H.; Atiquzzaman, M. et al. |volume=21 |issue=4 |pages=3723—68 |year=2019 |doi=10.1109/COMST.2019.2914094}}</ref><ref name="SehHealth20">{{cite journal |title=Healthcare Data Breaches: Insights and Implications |journal=Healthcare |author=Seh, A.H.; Zarour, M.; Alenezi, M. et al. |volume=8 |issue=2 |at=133 |year=2020 |doi=10.3390/healthcare8020133}}</ref><ref name="LiuEnhanc20">{{cite journal |title=Enhancing Privacy and Data Security across Healthcare Applications Using Blockchain and Distributed Ledger Concepts |journal=Healthcare |author=Liu, H.; Crespo, R.G.; Martinez, O.S. |volume=8 |issue=3 |at=243 |year=2020 |doi=10.3390/healthcare8030243}}</ref><ref name="DangASurv19">{{cite journal |title=A Survey on Internet of Things and Cloud Computing for Healthcare |journal=Electronics |author=Dang, L.M.; Piran, M.J.; Han, D. et al. |volume=8 |issue=7 |at=768 |year=2019 |doi=10.3390/electronics8070768}}</ref>: | |||
* '''Confidentiality''': Confidentiality is a process or mechanism of safeguarding patient health data from unauthorized access from public or internal users. Unauthorized access is dangerous and can potentially result in data leakage and can even cause serious damage to businesses. As the number of devices housing patient data increases, so does the potential threat (i.e., attack surface area) of exposing that data to external parties. Confidentiality is important in the healthcare industry, as the patient can be reluctant to give personal details to doctors if they are not confident the doctor's office will be able to keep that information confidential. By implementing access control and using encryption techniques, confidentiality can be achieved. | |||
* '''[[Data integrity]]''': Data integrity is required to ensure that data are not maliciously changed at any single point in time. This is especially important given that the [[Health Insurance Portability and Accountability Act]] (HIPAA) rules state that covered entities must implement procedures and policies to protect electronic healthcare information from improper destruction or alteration. Data integrity can be achieved by using a hashing mechanism or checksum for all data. This is most effectively done by implementing [[blockchain]] technology, as it is nearly impossible to change the hash of data with blockchain; it will change the entire chain if any of the hashes are changed. | |||
* '''Data availability''': Data availability says that information must be available at all times. Business-critical systems should be clustered or must have high availability to guarantee maximum uptime without service interruptions. | |||
* '''Data access violations and breaches''': These can negatively impact a business' public image and the the trust customers and partners have in the business. Intellectual property and sensitive data lost to these incidents can lead to other financial costs related to data forensics, communication to data owners, and more. | |||
* '''Inappropriate updates and fixes''': As cloud computing is a shared resource, any misconfiguration of the datacenter—a common cloud challenge—will potentially lead to compromising the customer data hosted within that datacenter. | |||
* '''Lack of security technologies''': The biggest challenge during the transition to cloud computing is the implementation of an appropriate security architecture to withstand cyberattacks. Unfortunately, this process remains a mystery for several organizations. Data are exposed to different threats when organizations assume that cloud migration is a “lift-and-shift” endeavor of simply porting their existing IT stack and security controls to a cloud environment. A lack of knowledge of the shared security responsibility is also a contributing factor. | |||
* '''Account hijacking''': Whether by "phishing," cloud system exploit, or direct attacks on a system, an internal user account can become compromised by an external actor, giving them access to sensitive information. | |||
* '''Insider threat''': In-house personnel can also perform malicious attacks on company assets by hacking servers or accessing and saving sensitive patient data, company emails, and more from insufficiently secured devices and programs. | |||
* '''Unsecured APIs''': Cloud computing providers develop a range of user software and APIs to allow customers to manage and interact with cloud services. The security and availability of standard cloud services are linked to the security of those APIs. Poorly designed APIs can lead to misuse or theft of information. Exposed, broken, and hacked APIs inevitably lead to realized data breaches. | |||
These challenges and others highlight the need for healthcare systems to understand the security and regulatory requirements necessary for keeping data and information safe in the cloud. | |||
==Classification of security solutions in eHealth systems== | |||
===Cryptographic security=== | |||
The continued advancement of information technology and data communications strengthens the exchange of highly sensitive medical information. Electronic health systems are widely used, and many medical facilities rely on the transmission and receipt of medical information online and across local networks. Over the years, many security systems have been introduced to monitor patient privacy and ensure the safety of interchangeable medical data. Cryptography is one of the primary techniques that provides security for eHealth systems. | |||
The cryptographic method allows various computations to take place directly from encrypted data, without the need to define them. As such, encryption schemes with homomorphic structures can be useful in building confidentiality agreements, where confidential information remains protected not only during exchange and storage, but also processing. | |||
Cryptography is a method of compiling and validating data, and then securely exchanging them, with the goal of keeping track of those data set up for them to investigate. Countless methods have been suggested to protect patient health care data. However, cryptographic methods can be seen in two forms: symmetric-key cryptography and asymmetric-key cryptography, where the former uses the same encryption and coding key while the latter uses different keys. These methods heavily rely on mechanisms such as public key encryption (PKE), symmetric key encryption (SKE), and a few native cryptographic devices used to protect the eHealth cloud. In the case of PKE, an open key or a pair of encryption and spelling keys are used; however, SKE-based methods use an equally shared private key as clearly defined in the PKE and SKE cryptography methods explained by Huang ''et al.''<ref name="HuangSecure18">{{cite journal |title=Secure Identity-Based Data Sharing and Profile Matching for Mobile Healthcare Social Networks in Cloud Computing |journal=IEEE Access |author=Huang, Q.; Yue, W.; He, Y. et al. |volume=6 |pages=36584–94 |year=2018 |doi=10.1109/ACCESS.2018.2852784}}</ref> | |||
====PKE, SKE, and other encryption methods==== | |||
In PKE schemes, two different key sets are considered: public key and secret key. Pairs of private and public data encryption and encryption keys are use with PKE, whereas SKE-based approaches use the same shared private key. Other cryptographic schemes include several encryption schemes such as attribute-based encryption (ABE), searchable encryption (SE), proxy encryption, homomorphic encryption, and identity-based encryption (IBE). | |||
Encryption is vital to data security. Encryption locks down electronic information so that no one other than the holder of the key can access the information. Encryption even works if the organizer breaks the organization’s security control on the information. The process involves encrypting data in one place, then transferring data over the network, and then deciphering data in the cloud, preventing data from being stolen during transfer. | |||
Cryptography and encryption have had a profound effect on the security of eHealth systems.<ref name="CelestiHowTo19">{{cite journal |title=How to Develop IoT Cloud e-Health Systems Based on FIWARE: A Lesson Learnt |journal=Journal of Sensor and Actuator Networks |author=Celesti, A.; Fazio, M.; Márquez, F.G. et al. |volume=8 |issue=1 |at=7 |year=2019 |doi=10.3390/jsan8010007}}</ref> There are some non-cryptographic methods that can also provide security, but these are not widely used as they provide partial security for the eHealth cloud under the security provided by crypto methods. Therefore, these systems are used with crypto methods in hybrid cloud systems. Other examples of encryption mechanisms include: | |||
* Broadcast encryption programs: This type of "stream" encryption allows a mid-stream broadcast website to securerly transmit data to an associate while minimizing the high-speed communications required.<ref name="SchizaProposal19">{{cite journal |title=Proposal for an eHealth Based Ecosystem Serving National Healthcare |journal=IEEE Journal of Biomedical and Health Informatics |author=Schiza, E.C.; Kyprianou, T.C.; Petkov, N. et al. |volume=23 |issue=3 |pages=1346–57 |year=2019 |doi=10.1109/JBHI.2018.2834230 |pmid=29993757}}</ref> | |||
* Qualified encryption: Privacy-based encryption can also be a form of public key cryptography in which the user’s private key and the security unit deletion of text definitions is only possible if the set of user key symbols matches the text symbols.<ref name="LinAMulti21">{{cite journal |title=A Multi-User Ciphertext Policy Attribute-Based Encryption Scheme with Keyword Search for Medical Cloud System |journal=Applied Sciences |author=Lin, H.-Y.; Jiang, Y.-R. |volume=11 |issue=1 |at=63 |year=2021 |doi=10.3390/app11010063}}</ref><ref name="MehmoodAuth19">{{cite journal |title=Authentication and Secure Key Management in E-Health Services: A Robust and Efficient Protocol Using Biometrics |journal=IEEE Access |author=Mehmood, Z.; Ghani, A.; Chen, G. et al. |volume=7 |pages=113385–97 |year=2019 |doi=10.1109/ACCESS.2019.2935313}}</ref> | |||
* Blockchain-based encryption: In the eHealth system, the verification, preservation, and synchronization of EMRs have always been a serious problem, and the random distribution of patient records will present various risks to the patient’s privacy. Placing hash counts in electronic medical data and keeping the corresponding value in the blockchain ensure its consistency and integrity. Khezr ''et al.'' demonstrate this using blockchain and Ethereum.<ref name="KhezrBlock19">{{cite journal |title=Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research |journal=Applied Sciences |author=Khezr, S.; Moniruzzaman, M.; Yassine, A. et al. |volume=9 |issue=9 |at=1736 |year=2019 |doi=10.3390/app9091736}}</ref> In their work, details listed in clinical records were removed from the Ethereum blockchain, and a good agreement was submitted to the Ethereum blockchain to accept the viewing of word searches instead of the third-party person.<ref name="KhezrBlock19" /> | |||
* Searchable symmetric encryption (SSE): SSE allows users transferring data to the cloud to query the data entered without the risk of data loss. Although interest in SSE is growing, current research does not examine how structures under SSE are constructed and how they end up in various areas of the SSE system. Most applications use a file table, where the appropriate file size and sublinear search can be done using the inverted file list. Direct referrals can only be obtained using the direct reference.<ref name="LiAchiev17">{{cite journal |title=Achieving Secure and Efficient Dynamic Searchable Symmetric Encryption over Medical Cloud Data |journal=IEEE Transactions on Cloud Computing |author=Li, H.; Yang, Y.; Dai, Y. et al. |volume=8 |issue=2 |pages=484–94 |year=2017 |doi=10.1109/TCC.2017.2769645}}</ref><ref name="ZhangSearch17">{{cite journal |title=Searchable Encryption for Healthcare Clouds: A Survey |journal=IEEE Transactions on Services Computing |author=Zhang, R.; Xue, R.; Liu, L. |volume=11 |issue=6 |pages=978–96 |year=2017 |doi=10.1109/TSC.2017.2762296}}</ref> | |||
===Access control management=== | |||
Another type of security mechanism for cloud-based eHealth is the access control management (AAM) system, where the server identifies users and determines their access rights. Authorized users then receieve tokens to access their sensitive records stored in the cloud.<ref name="EdemacuCollab20">{{cite journal |title=Collaborative Ehealth Privacy and Security: An Access Control With Attribute Revocation Based on OBDD Access Structure |journal=IEEE Journal of Biomedical and Health Informatics |author=Edemacu, K.; Jang, B.; Kim, J.W. |volume=24 |issue=10 |pages=2960-2972 |year=2020 |doi=10.1109/JBHI.2020.2973713 |pmid=32071017}}</ref><ref name="TongCloud14">{{cite journal |title=Cloud-assisted mobile-access of health data with privacy and auditability |journal=IEEE Journal of Biomedical and Health Informatics |author=Tong, Y.; Sun, J.; Chow, S.S.M. et al. |volume=18 |issue=2 |pages=419–29 |year=2014 |doi=10.1109/JBHI.2013.2294932 |pmid=24608047}}</ref> | |||
===Integrated blockchain model=== | |||
Kurdi ''et al.'' proposed an integrated blockchain model of a fully independent blockchain (FPB) and consortium blockchain (CB) as a means to improve the time taken for data validation.<ref name="KurdiHealthy19">{{cite journal |title=HealthyBroker: A Trustworthy Blockchain-Based Multi-Cloud Broker for Patient-Centered eHealth Services |journal=Electronics |author=Kurdi, H.; Alsalmah, S.; Alatawi, A. et al. |volume=8 |issue=6 |at=602 |year=2019 |doi=10.3390/electronics8060602}}</ref> Here, FPB is used as an old database of health care facilities and CB is used to store medical data from all participating medical professionals, expanding the available options for deploying a eHealth cloud computing platform. | |||
While the confidentiality of data converted to the cloud between institutions is not processed, medical data remain sensitive. Electronic health applications include a shared distribution of digital information between providers and patients. This transfer is an end-to-end process that must be secured and managed regularly. As hackers continue to seek new vulnerabilities to take advantage of, any cloud-driven app should be updated frequently to stay ahead of threats. However, a balance must be struck between strong security, controlled with a simple yet effective authentication method, and making authorized access reasonably simple. Additionally, the level of security and the cost associated with it must be considered. Managing security for an EMR or some other eHealth system should be a relatively painless process that doesn't increase the premium of the solution. | |||
===Custom security solutions=== | |||
Table 1 shows a variety of custom approaches to eHealth systems security, as described in the literature. | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="80%" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" colspan="5"|'''Table 1.''' Custom approaches to eHealth systems security | |||
|- | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Reference | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Security and privacy | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|eHealth | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Cloud | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Contribution | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Griebel ''et al.'' 2015<ref name="GriebelAScoping15" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed secure personal eHealth system based on certificate CA to authorized users only | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Venčkauskas ''et al.'' 2016<ref name="VenčkauskasAModel16" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed a prototype-based personalised health monitoring application | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Khan 2020<ref name="KhanAnIoT20" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|x | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed a wearable IoT-enabled heart disease prediction system using the MDCNN classifier | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Yang and Hara-Azumi 2020<ref name="YangImplem20" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|x | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Addressed the development of IoT-based eHealth systems on both the hardware and software levels | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Chenthara ''et al.'' 2019<ref name="ChentharaSecurity19" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Explored efficient comprehensive security mechanisms for EHR and the techniques to maintain the integrity and confidentiality of patients’ information | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Kim ''et al.'' 2019<ref name="KimMPPDS19" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|x | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed a novel collaborative eHealth system, which supports multi-level privacy-preserving data sharing (MPPDS) | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Zhang ''et al.'' 2018<ref name="ZhangHealth18">{{cite journal |title=HealthDep: An Efficient and Secure Deduplication Scheme for Cloud-Assisted eHealth Systems |journal=IEEE Transactions on Industrial Informatics |author=Zhang, Y.; Xu, C.; Li, H. et al. |volume=14 |issue=9 |pages=4101–12 |year=2018 |doi=10.1109/TII.2018.2832251}}</ref> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed HealthDep, the first secure and efficient encrypted EMR deduplication scheme for cloud-assisted eHealth systems | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Yeh ''et al.'' 2018<ref name="YehCloud18">{{cite journal |title=Cloud-Based Fine-Grained Health Information Access Control Framework for Lightweight IoT Devices with Dynamic Auditing and Attribute Revocation |journal=IEEE Transactions on Cloud Computing |author=Yeh, L.-Y.; Chiang, P.-Y.; Tsai, Y.-L. et al. |volume=6 |issue=2 |pages=532–44 |year=2018 |doi=10.1109/TCC.2015.2485199}}</ref> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed a benchmark lossless method which is suitable for remoting health monitoring systems | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Avila ''et al.'' 2017<ref name="AvilaAppli17">{{cite journal |title=Applications Based on Service-Oriented Architecture (SOA) in the Field of Home Healthcare |journal=Sensors |author=Avila, K.; Sanartin, P.; Jabba, D. et al. |volume=17 |issue=8 |at=1703 |year=2017 |doi=10.3390/s17081703}}</ref> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Reviewed the applications developed in the health industry which are focused on patient care from home and implemented a service-oriented architecture (SOA) design | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Guo ''et al.'' 2014<ref name="GuoAPrivacy14">{{cite journal |title=A Privacy-Preserving Attribute-Based Authentication System for Mobile Health Networks |journal=IEEE Transactions on Mobile Computing |author=Guo, L.; Zhang, C.; Sun, J. et al. |volume=13 |issue=9 |pages=1927–41 |year=2014 |doi=10.1109/TMC.2013.84}}</ref> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Provided an answer for privacy-preserving knowledge storage by group action of PRF-based key management for unlikability, a research and access pattern concealment theme supported redundancy, and a secure assortment technique for privacy conserving keyword search | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Liu ''et al.'' 2018<ref name="LiuSecure18">{{cite journal |title=Secure and fine-grained access control on e-healthcare records in mobile cloud computing |journal=Future Generation Computer Systems |author=Liu, Y.; Zhang, Y.; Ling, J. et al. |volume=78 |issue=3 |pages=1020–26 |year=2018 |doi=10.1016/j.future.2016.12.027}}</ref> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|✓ | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Proposed automatic internet of things (IoT) building blocks to exchange the information between devices and integrated cloud computing | |||
|- | |||
|} | |||
|} | |||
==Proposed solutions for security in cloud-based eHealth systems== | |||
The conventional approach to healthcare practices in the world has been changed by the growth of information and communication technologies. In the partial abandonment of paper-based medical procedures for more electronic procedures, this development is well noticed, particularly in most developed countries of the world. The need to federate and integrate electronic health information from medical research [[Laboratory|laboratories]], hospitals, and health insurance companies has led to the development of a concept called electronic health or eHealth.<ref name="EgendiImprov18">{{cite journal |title=Improving Remote Health Monitoring: A Low-Complexity ECG Compression Approach |journal=Diagnostics |author=Elgendi, M.; Al-Ali, A.; Mohamed, A. et al. |volume=8 |issue=1 |at=10 |year=2018 |doi=10.3390/diagnostics8010010}}</ref> Simply put, eHealth can be defined as the use of information technology (IT) and e-commerce practices for health information processing, sharing, and management. However, these aspects can be difficult to manage in a cloud-based environment that enables the collaborative sharing of medical information across multiple administrative domains by multiple users.<ref name="LiagkouAttack19">{{cite journal |title=Attack Detection for Healthcare Monitoring Systems Using Mechanical Learning in Virtual Private Networks over Optical Transport Layer Architecture |journal=Computation |author=Liagkou, V.; Kavvadas, V.; Chronopoulos, S.K. et al. |volume=7 |issue=2 |at=24 |year=2019 |doi=10.3390/computation7020024}}</ref> | |||
To be sure, cloud computing has many benefits, including the timely and seamless transfer and sharing of medical information across geophysical boundaries. Cloud computing also simplifies the management of infrastructure for healthcare providers and has provided them with ample opportunity to familiarize themselves with IT and cloud service providers. Various academic papers have established cloud computing as having numerous advantages, including scalability, cost-effectiveness, greater agility, and improved collaborative resource sharing.<ref name="AbuKhousaEHealth12">{{cite journal |title=e-Health Cloud: Opportunities and Challenges |journal=Future Internet |author=AbuKhousa, E.; Mohamed, N.; Al-Jaroodi, J. |volume=4 |issue=3 |pages=621–45 |year=2012 |doi=10.3390/fi4030621}}</ref> | |||
However, despite the various advantages, there are also security and privacy challenges that urgently deserve the utmost attention for the realization of cloud computing's efficient and full-scale use.<ref name="SahmimPrivacy17">{{cite journal |title=Privacy and Security in Internet-based Computing: Cloud Computing, Internet of Things, Cloud of Things: A review |journal=Procedia Computer Science |author=Sahmim, S.; Gharsellaoui, H. |volume=112 |pages=1516–22 |year=2017 |doi=10.1016/j.procs.2017.08.050}}</ref> On several occasions, cryptographic and non-cryptographic approaches have been used to ensure the preservation of cloud computing security and the privacy of health information. In addition, fine-grained as well as patient-centric access control systems are frequently used to achieve electronic health privacy. This paper has reviewed these different data security measures and discussed their strengths and weaknesses. Additionally, efforts have been made to provide examples of better options for securing eHealth information. | |||
==Research issues and future directions== | |||
Going forward, several privacy and security issues related to EHRs and their shared use must be addressed. EHR data are extremely sensitive, confidential, and in particular, are stored on third-party servers, leading to significant risks in terms of data privacy and security. Some of the major concerns that require further action include: | |||
* developing processes and procedures on how to protect and secure EHR data stored in the cloud; | |||
* using confidential EHR and other health care data via the cloud; and | |||
* determining the best encryption system that can be used to maintain EHR data security in the cloud. | |||
The above points are not limited to EHR data and extend to other eHealth systems. This highlights the need to use secure infrastructure in eHealth systems that will ensure the privacy and security of data and thus protect patient privacy and trust. The level of privacy required is high, making privacy considerations one of the most important aspects of the healthcare industry. Maintaining confidentiality through the sharing and used of medical records is essential to detecting and preventing fraud. Keeping track of data sources and programs is advisable. | |||
The recommendations behind this research can be further enhanced by verifying user authenticity and privacy in cloud-based big data. A secure authentication method that incorporates tree-based hashing in the authorization structure, used for user authentication during multi-level configuration, resists fraudulent attacks and protects privacy. The authoritative structure of hierarchical attributes leads to a lot of confusion and significant problems. Artificial intelligence or big data analytics (BDA) could incorporate system design controls for each process. More recently, the usefulness of replica nodes has emerged. Leaked user data is displayed with random action keys in secure data connections. By using analytics tools, patient data can be merged into a single dashboard view, potentially improving patient outcomes. | |||
==Conclusions== | |||
Healthcare has already adopted cloud-based solutions to solve multiple problems cost-effectively. While considering the future and growth of cloud-based healthcare services, we focused on the security of critical EHRs and other eHealth systems and proposed an identity-based secure and encrypted data-sharing technique. We have studied the existing PKE, IBE, IBBE, and ABE methods and then proposed multiple solutions to safeguard cloud-based data in eHealth systems. Appropriate security solutions should be developed and maintained to protect data security. The future of cloud-based eHealth services will be the integration of file-based and cloud-based applications that integrate a computer-based hybrid IT solution that measures the flexibility and scalability associated with cloud management and healthcare data security. This review highlights a comprehensive study of existing cloud-based eHealth solutions that incorporate cryptographic and non-cryptographic methods for protecting the privacy and security of digital data. | |||
==Acknowledgements== | |||
We thank the anonymous reviewers for their valuable comments and suggestions, which helped us to improve the content of our paper. | |||
===Author contributions=== | |||
R.S. and Z.A.Z.; methodology: R.S.; data curation: R.S.; resources: R.S.; writing—original draft preparation: R.S.; writing—review and editing: R.S. and Z.A.Z.; supervision. All authors have read and agreed to the published version of the manuscript. | |||
===Funding=== | |||
This research received no external funding. | |||
===Conflicts of interest=== | |||
The authors declare no conflict of interest. | |||
==References== | ==References== | ||
| Line 65: | Line 286: | ||
==Notes== | ==Notes== | ||
This presentation is faithful to the original, with only a few minor changes to presentation. However, extensive grammar, punctuation, and idea organization and clean up was required to improve the readability of the original article. In some cases important information was missing from the references, and that information was added. The original citation seven (Huh 2018) was omitted in this version as it appeared to have no connection to the topic cited. A paragraph appearing in the original introduction involving "mists" and service level agreements also had no bearing to the paper and appears to have been accidentally included in the original; it is omitted for this version. | This presentation is faithful to the original, with only a few minor changes to presentation. However, extensive grammar, punctuation, and idea organization and clean up was required to improve the readability of the original article. In some cases important information was missing from the references, and that information was added. The original citation seven (Huh 2018) was omitted in this version as it appeared to have no connection to the topic cited. A paragraph appearing in the original introduction involving "mists" and service level agreements also had no bearing to the paper and appears to have been accidentally included in the original; it is omitted for this version. The original includes material from [https://www.sciencedirect.com/science/article/pii/S1110866517302797 Azeez and Van der Vyver 2019] in the "Proposed solutions for security in cloud-based eHealth systems" section; that content was omitted for this version as it appears inadvertent or plagiarized. Finally, the Discussion in the original is a complete disaster, referencing numerous articles that aren't even discussed or cited (e.g., a mention of [https://doi.org/10.1016/j.future.2017.02.014 Rahmani ''et al.'''s UT-Gate], as well as more almost-plagiarized content from [https://www.sciencedirect.com/science/article/pii/S1110866517302797 Azeez and Van der Vyver 2019]). The discussion was completely removed for this version as it too appears to be inadvertent or plagiarized content. | ||
<!--Place all category tags here--> | <!--Place all category tags here--> | ||
Latest revision as of 20:49, 19 September 2021
| Full article title | Security and privacy in cloud-based eHealth systems |
|---|---|
| Journal | Symmetry |
| Author(s) | Sivan, Remya; Zukarnain, Zuriati A. |
| Author affiliation(s) | University Putra Malaysia |
| Primary contact | Email: gs59108 at student dot upm dot edu dot my |
| Year published | 2021 |
| Volume and issue | 13(5) |
| Article # | 742 |
| DOI | 10.3390/sym13050742 |
| ISSN | 2073-8994 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2073-8994/13/5/742/htm |
| Download | https://www.mdpi.com/2073-8994/13/5/742/pdf (PDF) |
Abstract
Cloud-based healthcare computing has changed the face of healthcare in many ways. The main advantages of cloud computing in healthcare are scalability of the required service and the provision to upscale or downsize the data storge, particularly in conjunction with approaches to artificial intelligence (AI) and machine learning. This paper examines various research studies to explore the utilization of intelligent techniques in health systems and mainly focuses on the security and privacy issues in the current technologies. Despite the various benefits related to cloud computing applications for healthcare, there are different types of management, technology handling, security measures, and legal issues to be considered and addressed. The key focus of this paper is to address the increased demand for cloud computing and its definition, technologies widely used in healthcare, their problems and possibilities, and the way protection mechanisms are organized and prepared when the company chooses to implement the latest evolving service model. As such, we sought out current literature on different approaches and mechanisms used in eHealth to deal with security and privacy issues. Some of these approaches have strengths and weaknesses. After selecting original articles, a literature review was carried out, and we identified several models adopted in their solutions. We arrived at the reviewed articles after comparing the models used.
Keywords: eHealth, cloud computing, security, privacy in health systems
Introduction
Innovative changes in science, technology, and the broad understanding of our universe have permitted the evolution of practical, progressive answers to enhance the nature of human existence. Researchers considering these innovative developments have identified and assessed wellbeing data from various sources to acquire actionable information and address issues concerning human wellbeing, particularly in the realm of healthcare. In this manner, the advancement of incorporated medical care innovations—including technological innovations—has the likelihood to enhance efficiency and improve understanding of the results at each level of the medical care framework. Long-term care (LTC) facilities are a crucial a part of the healthcare industry, providing care to the fastest-growing group of the population. However, the adoption of electronic health records (EHRs) in LTC facilities lags behind other areas of the health care industry.[1] The advancement of new electronic health (eHealth) application frameworks can take care of specific issues pertinent to conventional medical care frameworks by means of powerful patient wellbeing controls, pervasive information access, distant patient checking, quick clinical intercession, and decentralized electronic medical records (EMRs). These frameworks can oversee wellbeing data and patient information, upgrade personal satisfaction, increase coordinated effort, improve results, decrease expenses, and increase the general efficiency of electronic healthcare administrations.[2] For healthcare, EHRs are required to be shared among different healthcare organizations, medical drug manufacturers, pharmacists, medical insurance providers, researchers, and patients. This poses a significant challenge to keeping patients' sensitive data secure.[3] Eisenach highlights this in his depiction of eHealth as a tech industry that addresses the intersection of the internet, systems administration, and medical services, which has the potential to benefit the framework of clients and partners. The growing concept of eHealth involves the convergence of clinical informatics, general human wellbeing, and the wellbeing and the use of a secure internet, which helps drive the overall advancement of new innovation to tackle profound issues, drive down expenses, and improve understanding.[4]
Along these lines, models, gadgets, and frameworks associated with the internet of things (IoT) have become universal. Besides, the broad appropriation of IoT has harmonized with the improvement of interrelated, corresponding advances, for example, registering knowledge for medical care, business, industry, operational frameworks, etc. The efficient and safe usage of wellbeing data advancements, benefits, and all-encompassing eHealth frameworks requires exceedingly efficient and strong security frameworks to make such execution reasonable. The universality of IoT frameworks has driven the expansion of IoT innovation, remembering assorted designs for use by healthcare organizations. Connecting networks, gadgets, applications, and administration with IoT permits eHealth frameworks to share related data by utilizing the most recent IoT innovations.[5]
IoT and distributed computing are progressive innovations that supplement each other’s capacities when incorporated as flexible, versatile, and efficient tolerant medical service frameworks. The blend provides benefits, including simplicity of execution (contrasted with regular organizations), improved data security during correspondence, speedy access to records, and lower energy costs over customary modalities. Cloud-based IoT eHealth frameworks can significantly improve medical care benefits and advance persistent and efficient healthcare development. Within such frameworks, hidden IoT networks empower correspondence between clients, administrators, and workers, with clinical information being stored in the cloud. However, with new these improvements in distributed computing pushing healthcare beyond "business as usual," a variety of data storage and security issues are revealed, requiring consideration.[6]
Distributed and cloud computing are innovations that have and continue to transform the healthcare industry. Distributed computing can help improve a healthcare organization's adaptability, savvy, finances, data processing ability, and secure data sharing and distribution.[7] Cloud computing, when implemented well, should provide the ability to oversee applications and information, server accessibility, and end-used computing (EUC). Cloud computing should also ideally provide a complete, logical set of insights into a healthcare enterprise's infrastructure and end clients. By extension, cloud computing permits staff or workers to obtain and deal with their applications and information continuously on any gadget, from anywhere in the world with access to the internet.[8] However, we recognize that a coordinated effort to move information to distributed systems and the cloud brings serious security and protection worries for healthcare providers. As such, they must endeavor to fully address the effectiveness of, security of, and versatility associated with the introduction of cloud-based eHealth to the healthcare enterprise.
The fundamental motivation behind this paper is to examine the idea of cloud-based eHealth, the current utilization of eHealth in healthcare, and the challenges and solutions of cloud-based eHealth. This paper will walk through the state of distributed and cloud computing within the healthcare industry, along with the diverse opportunities and significant cloud-related security challenges associated with it. Additionally, we will discuss the plausible security arrangements for cloud-enabled eHealth.
Methods and materials
The existing literature on eHealth security is difficult to survey. We originally identified and downloaded 40 papers from the ACM Digital Library, 57 articles from the IEEE Computer Society's Digital Library, and 43 from the IEEE Xplore library to provide a fair and calculable number of articles surveyed. Additional articles were also accessed from the specialized repositories of Springer, Elsevier, Science Direct, and MDPI. Few other papers from other sources were used as those sources were not as well-known and respected as from those cited. Of those papers analyzed, we identified 110 publications worthy of use in the face of conflicting evaluation models and methods used by many analysts. Due to the similarities found in the models obtained by some scientists, the analyzed papers were restricted to the momentum number.
We then directly analyzed the papers, looking at and dissecting the strengths of each of the approaches obtained in seeking a solution to the security problem in eHealth. Through this process, we identified numerous shortcomings of the various proposed techniques, which eventually indicated a way forward to mitigate eHealth security incidents. Improving healthcare outcomes using eHealth is a developing area at the crossroads of clinical informatics, general human wellbeing, and patient health data that is securely communicated and enhanced through the internet and related technologies.[9][10][11][12] The use of eHealth in the healthcare setting represents not olny a specialized turn of events from a more traditional approach, but also a perspective, a demeanor, and a duty for coordinated, national efforts to enhance patient care through the use of information and communication technologies locally, territorially, and internationally.[13]
Research strategy
As this was a comprehensive review, we aimed to update the findings of previous studies (54) regarding the same matter. We retrieved eligible studies from late 2013 to December 2020. The study selection searched for publications from the journal Symmetry, other journals in MDPI, IEEE Access, and other IEEE journals. The first step involved including the relevant articles with related keywords in the title or abstract based on the inclusion criteria. Papers not related to our study were excluded. The second step consisted of a full text screening of the relevant studies to select the most eligible articles.
Research questions
When screening papers, we also wanted to ensure they would help us address four important questions:
- What is cloud computing and the state of the art of the cloud-based computing solutions commonly used in healthcare systems?
- What are the security concerns or challenges in cloud-based computing in healthcare systems?
- How are the current cloud-based eHealth systems being protected?
- What is the best solution for security in cloud-based eHealth systems?
Cloud computing and the state of the art
Cloud computing—a set of internet-based, always-on computing services provisioned on an as-needed or continuous basis—is organized into three different service models: infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
IaaS is a cloud service model that delivers computing resources, networking, and storage to consumers. It enables end users to upscale or downsize resources on an as-needed basis, reducing the need for compute upscaling, up-front capital expenditures, and unnecessary infrastructure.[14][15] PaaS is a cloud service model that provides an application development and deployment environment to comsumers. PaaS platforms handle the complexity around operating systems and servers and leaves application developers more time to focus their business requirements to the software they are developing. SaaS is a cloud service model that delivers software to customers with relative ease; all you need is an internet connection and a browser. This service model requires the cloud vendor to manage most of their technical issues, meaning customers need not heavily lean on their in-house IT expertise for hosting and maintaining the software.
Figure 1 take a high-level look at these cloud infastructures, as compared with on-premises offerings. Light blue indicates customer responsibility, and dark blue indicates cloud provider responsibility.
|
The eHealth system is a newly developed space that contains electronic processes and communications. EHRs and EMRs act as a compilation of digital patient health data, containing demographic information, diagrams, patient medical information, patient medications, hospital or clinic reports, radiology photographs, billing information, and other sensitive patient information. Cloud computing offers a cost-effective way of effectively storing, processing, and updating that type of data with efficiency and quality.[16] Cloud computing also offers the advantage of access to hosted services from multiple locations around the world with by multiple users.
Separately, eHealth systems promise faster, robust, and sought-after access to medical records, fewer medical regulations, and improved health care quality, though they also should ideally maintain patient privacy, prevent improper authorization, and prevent misuse of sensitive patient data. When using these eHealth systems in the cloud, maintaining security and privacy are especially critical when sharing or accessing patient data. An overview of e-health structures in the scope of cloud computing is shown in Figure 2.
|
There are a number of deployment models for cloud computing, including public cloud, private cloud, and hybrid cloud. Public cloud deployments make resources available to private and public users via the internet as an ongoing or on-demand service, allowing clients to pay only for what they use or subscribe to. Instead of purchasing a physical server and networking equipment, a public cloud customer can purchase a virtual server and network that can be accessed from anywhere. The public cloud relies on a customized environment to provide corporate infrastructure expansion, allowing the company to host certain aspects of its infrastructure and services on virtual and identifiable third-party servers. Public cloud service providers have unique capabilities, and they offer excellent types of services and price models. However, companies considering migration to public cloud must carefully consider their options when it comes to choosing a provider, especially if there is a possibility of service being preemptively terminated in a long-term contract. Careful planning can help reduce the cost of monthly payments for cloud services, but organizations with unplanned or unexpected usage requirements may find it difficult to avoid spending large sums on public cloud services.[17]
Private clouds are cloud installations used exclusively by a single organization and its authorized users, usually in the form of a single network or datacenter that provides services hosted to a specific group of people. Private clouds offer easy access and more control over security for the organizations using them. Although a private cloud is less expensive than using a public cloud, the cost is not easily measured. The development or growth of private cloud infrastructure will require the purchase of additional equipment. Similarly, when the need for a private cloud decreases, expensive resources and equipment are inevitably misused.[18][19]
A hybrid cloud infrastructure is a combination of two or more integrated public and private clouds. In hybrid cloud infrastructure, the organization provides and manages their own resources within the private data center while also using additional outsourced public and private services—such as VMware that works in tandem with Fortinet Networks—to provide a hybrid cloud infrastructure that allows for increased organizational security on private and remote servers while the public cloud is largely secured by the cloud provider. Hybrid cloud is usually an excellent deal for those debating between a public cloud and a private cloud. The hybrid cloud environment allows organizations to take advantage of both types of cloud platforms and choose which cloud will provide the specific data needs. For example, the hybrid cloud provides another way to store sensitive company data and information, allowing the organization to maintain sensitive security configurations in the private cloud while conducting other business activities in the public cloud.[20][21]
Advantages of cloud-based eHealth systems
The more a healthcare center integrates system data and information via a global computer network such as the internet, the more global risk that is placed into the information network due to the expansion of breachable information access points. The need to access sensitive patient information should be limited to authorized users and protected from illegal users who may misuse that information for a variety of purposes. Identity-based encryption (IBE) has so far proven to be one of the best security solutions to protect eHealth record data.[22][23] The encryption algorithm deals with problems found in common cryptographic techniques using any thread as a public key. The system can further enhance the security of health records by adding authentication procedures to three connected servers. In this system, communication between three servers uses IBE to encrypt data, such that each server can perform the encryption and decryption process during the data exchange. Only servers with authorized IDs can access and extract health record data. Currently, test results show performance relative to the speed of the algorithm used in the system.[24][25]
As discussed here, and by Vilela et al.[26], cloud storage involves sending data over the internet to a remote cloud data center for storage. Cloud storage is delivered according to demand, capacity, and cost requirements, giving the customer control over how they invest in and manage their data storage infrastructure. This model has the advantage of lending speed, scale, and durability to an organization's eHealth data management.
Running eHealth systems in the cloud has additional advantages as well, including:
- Ease of access using a web browser and integrated single sign-on (SSO)
- No requirement for a virtual private network (VPN) to access other sites or networks
- Simplified data management and on-demand scalability
- No overhead cost to maintain the physical infrastructure
- No hardware-related post-warranty charges for the physical infrastructure
- Little to no additional power consumption
Mechanism commonly used in the cloud also lend to eHealth systems. For example, one of the major schemes in healthcare systems is attribute-based encryption for data. Encryption provides high-class access control for every user, as well as revocation, scalability, dynamic user management, and traceability. Users have high-grade login access, which can be integrated with two-factor authentication (2FA) as well as one-time passwords (OTP) for every access. Similarly, users’ access can be revoked from a centralized management console at any point in time by the administrator. The most important advantage is that every access can be recorded and traced, and clipping can be implemented for each session.[27] Privileged access management (PAM) is another technology which can be used if there are many subsystems that a user needs to access at a single point in time.
Another cloud-based scheme for eHealth systems involves robust and secure access control, which resolves single-point performance bottleneck problems. This solves the majority of security access control issues, as the certificate needs to be trusted and issued from a certified hosting platform. The main disadvantage, however, is that there is no process or mechanism for attribute revocation.
Security issues of cloud-based eHealth systems
Despite the advantages cloud computing brings to eHealth, it still has its own security challenges which emerge from time to time due to inadequate compliance with proper security protocols and best practices. Some of those challenges include[28][29][30][31][32]:
- Confidentiality: Confidentiality is a process or mechanism of safeguarding patient health data from unauthorized access from public or internal users. Unauthorized access is dangerous and can potentially result in data leakage and can even cause serious damage to businesses. As the number of devices housing patient data increases, so does the potential threat (i.e., attack surface area) of exposing that data to external parties. Confidentiality is important in the healthcare industry, as the patient can be reluctant to give personal details to doctors if they are not confident the doctor's office will be able to keep that information confidential. By implementing access control and using encryption techniques, confidentiality can be achieved.
- Data integrity: Data integrity is required to ensure that data are not maliciously changed at any single point in time. This is especially important given that the Health Insurance Portability and Accountability Act (HIPAA) rules state that covered entities must implement procedures and policies to protect electronic healthcare information from improper destruction or alteration. Data integrity can be achieved by using a hashing mechanism or checksum for all data. This is most effectively done by implementing blockchain technology, as it is nearly impossible to change the hash of data with blockchain; it will change the entire chain if any of the hashes are changed.
- Data availability: Data availability says that information must be available at all times. Business-critical systems should be clustered or must have high availability to guarantee maximum uptime without service interruptions.
- Data access violations and breaches: These can negatively impact a business' public image and the the trust customers and partners have in the business. Intellectual property and sensitive data lost to these incidents can lead to other financial costs related to data forensics, communication to data owners, and more.
- Inappropriate updates and fixes: As cloud computing is a shared resource, any misconfiguration of the datacenter—a common cloud challenge—will potentially lead to compromising the customer data hosted within that datacenter.
- Lack of security technologies: The biggest challenge during the transition to cloud computing is the implementation of an appropriate security architecture to withstand cyberattacks. Unfortunately, this process remains a mystery for several organizations. Data are exposed to different threats when organizations assume that cloud migration is a “lift-and-shift” endeavor of simply porting their existing IT stack and security controls to a cloud environment. A lack of knowledge of the shared security responsibility is also a contributing factor.
- Account hijacking: Whether by "phishing," cloud system exploit, or direct attacks on a system, an internal user account can become compromised by an external actor, giving them access to sensitive information.
- Insider threat: In-house personnel can also perform malicious attacks on company assets by hacking servers or accessing and saving sensitive patient data, company emails, and more from insufficiently secured devices and programs.
- Unsecured APIs: Cloud computing providers develop a range of user software and APIs to allow customers to manage and interact with cloud services. The security and availability of standard cloud services are linked to the security of those APIs. Poorly designed APIs can lead to misuse or theft of information. Exposed, broken, and hacked APIs inevitably lead to realized data breaches.
These challenges and others highlight the need for healthcare systems to understand the security and regulatory requirements necessary for keeping data and information safe in the cloud.
Classification of security solutions in eHealth systems
Cryptographic security
The continued advancement of information technology and data communications strengthens the exchange of highly sensitive medical information. Electronic health systems are widely used, and many medical facilities rely on the transmission and receipt of medical information online and across local networks. Over the years, many security systems have been introduced to monitor patient privacy and ensure the safety of interchangeable medical data. Cryptography is one of the primary techniques that provides security for eHealth systems.
The cryptographic method allows various computations to take place directly from encrypted data, without the need to define them. As such, encryption schemes with homomorphic structures can be useful in building confidentiality agreements, where confidential information remains protected not only during exchange and storage, but also processing.
Cryptography is a method of compiling and validating data, and then securely exchanging them, with the goal of keeping track of those data set up for them to investigate. Countless methods have been suggested to protect patient health care data. However, cryptographic methods can be seen in two forms: symmetric-key cryptography and asymmetric-key cryptography, where the former uses the same encryption and coding key while the latter uses different keys. These methods heavily rely on mechanisms such as public key encryption (PKE), symmetric key encryption (SKE), and a few native cryptographic devices used to protect the eHealth cloud. In the case of PKE, an open key or a pair of encryption and spelling keys are used; however, SKE-based methods use an equally shared private key as clearly defined in the PKE and SKE cryptography methods explained by Huang et al.[33]
PKE, SKE, and other encryption methods
In PKE schemes, two different key sets are considered: public key and secret key. Pairs of private and public data encryption and encryption keys are use with PKE, whereas SKE-based approaches use the same shared private key. Other cryptographic schemes include several encryption schemes such as attribute-based encryption (ABE), searchable encryption (SE), proxy encryption, homomorphic encryption, and identity-based encryption (IBE).
Encryption is vital to data security. Encryption locks down electronic information so that no one other than the holder of the key can access the information. Encryption even works if the organizer breaks the organization’s security control on the information. The process involves encrypting data in one place, then transferring data over the network, and then deciphering data in the cloud, preventing data from being stolen during transfer.
Cryptography and encryption have had a profound effect on the security of eHealth systems.[34] There are some non-cryptographic methods that can also provide security, but these are not widely used as they provide partial security for the eHealth cloud under the security provided by crypto methods. Therefore, these systems are used with crypto methods in hybrid cloud systems. Other examples of encryption mechanisms include:
- Broadcast encryption programs: This type of "stream" encryption allows a mid-stream broadcast website to securerly transmit data to an associate while minimizing the high-speed communications required.[35]
- Qualified encryption: Privacy-based encryption can also be a form of public key cryptography in which the user’s private key and the security unit deletion of text definitions is only possible if the set of user key symbols matches the text symbols.[36][37]
- Blockchain-based encryption: In the eHealth system, the verification, preservation, and synchronization of EMRs have always been a serious problem, and the random distribution of patient records will present various risks to the patient’s privacy. Placing hash counts in electronic medical data and keeping the corresponding value in the blockchain ensure its consistency and integrity. Khezr et al. demonstrate this using blockchain and Ethereum.[38] In their work, details listed in clinical records were removed from the Ethereum blockchain, and a good agreement was submitted to the Ethereum blockchain to accept the viewing of word searches instead of the third-party person.[38]
- Searchable symmetric encryption (SSE): SSE allows users transferring data to the cloud to query the data entered without the risk of data loss. Although interest in SSE is growing, current research does not examine how structures under SSE are constructed and how they end up in various areas of the SSE system. Most applications use a file table, where the appropriate file size and sublinear search can be done using the inverted file list. Direct referrals can only be obtained using the direct reference.[39][40]
Access control management
Another type of security mechanism for cloud-based eHealth is the access control management (AAM) system, where the server identifies users and determines their access rights. Authorized users then receieve tokens to access their sensitive records stored in the cloud.[41][42]
Integrated blockchain model
Kurdi et al. proposed an integrated blockchain model of a fully independent blockchain (FPB) and consortium blockchain (CB) as a means to improve the time taken for data validation.[43] Here, FPB is used as an old database of health care facilities and CB is used to store medical data from all participating medical professionals, expanding the available options for deploying a eHealth cloud computing platform.
While the confidentiality of data converted to the cloud between institutions is not processed, medical data remain sensitive. Electronic health applications include a shared distribution of digital information between providers and patients. This transfer is an end-to-end process that must be secured and managed regularly. As hackers continue to seek new vulnerabilities to take advantage of, any cloud-driven app should be updated frequently to stay ahead of threats. However, a balance must be struck between strong security, controlled with a simple yet effective authentication method, and making authorized access reasonably simple. Additionally, the level of security and the cost associated with it must be considered. Managing security for an EMR or some other eHealth system should be a relatively painless process that doesn't increase the premium of the solution.
Custom security solutions
Table 1 shows a variety of custom approaches to eHealth systems security, as described in the literature.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Proposed solutions for security in cloud-based eHealth systems
The conventional approach to healthcare practices in the world has been changed by the growth of information and communication technologies. In the partial abandonment of paper-based medical procedures for more electronic procedures, this development is well noticed, particularly in most developed countries of the world. The need to federate and integrate electronic health information from medical research laboratories, hospitals, and health insurance companies has led to the development of a concept called electronic health or eHealth.[49] Simply put, eHealth can be defined as the use of information technology (IT) and e-commerce practices for health information processing, sharing, and management. However, these aspects can be difficult to manage in a cloud-based environment that enables the collaborative sharing of medical information across multiple administrative domains by multiple users.[50]
To be sure, cloud computing has many benefits, including the timely and seamless transfer and sharing of medical information across geophysical boundaries. Cloud computing also simplifies the management of infrastructure for healthcare providers and has provided them with ample opportunity to familiarize themselves with IT and cloud service providers. Various academic papers have established cloud computing as having numerous advantages, including scalability, cost-effectiveness, greater agility, and improved collaborative resource sharing.[51]
However, despite the various advantages, there are also security and privacy challenges that urgently deserve the utmost attention for the realization of cloud computing's efficient and full-scale use.[52] On several occasions, cryptographic and non-cryptographic approaches have been used to ensure the preservation of cloud computing security and the privacy of health information. In addition, fine-grained as well as patient-centric access control systems are frequently used to achieve electronic health privacy. This paper has reviewed these different data security measures and discussed their strengths and weaknesses. Additionally, efforts have been made to provide examples of better options for securing eHealth information.
Research issues and future directions
Going forward, several privacy and security issues related to EHRs and their shared use must be addressed. EHR data are extremely sensitive, confidential, and in particular, are stored on third-party servers, leading to significant risks in terms of data privacy and security. Some of the major concerns that require further action include:
- developing processes and procedures on how to protect and secure EHR data stored in the cloud;
- using confidential EHR and other health care data via the cloud; and
- determining the best encryption system that can be used to maintain EHR data security in the cloud.
The above points are not limited to EHR data and extend to other eHealth systems. This highlights the need to use secure infrastructure in eHealth systems that will ensure the privacy and security of data and thus protect patient privacy and trust. The level of privacy required is high, making privacy considerations one of the most important aspects of the healthcare industry. Maintaining confidentiality through the sharing and used of medical records is essential to detecting and preventing fraud. Keeping track of data sources and programs is advisable.
The recommendations behind this research can be further enhanced by verifying user authenticity and privacy in cloud-based big data. A secure authentication method that incorporates tree-based hashing in the authorization structure, used for user authentication during multi-level configuration, resists fraudulent attacks and protects privacy. The authoritative structure of hierarchical attributes leads to a lot of confusion and significant problems. Artificial intelligence or big data analytics (BDA) could incorporate system design controls for each process. More recently, the usefulness of replica nodes has emerged. Leaked user data is displayed with random action keys in secure data connections. By using analytics tools, patient data can be merged into a single dashboard view, potentially improving patient outcomes.
Conclusions
Healthcare has already adopted cloud-based solutions to solve multiple problems cost-effectively. While considering the future and growth of cloud-based healthcare services, we focused on the security of critical EHRs and other eHealth systems and proposed an identity-based secure and encrypted data-sharing technique. We have studied the existing PKE, IBE, IBBE, and ABE methods and then proposed multiple solutions to safeguard cloud-based data in eHealth systems. Appropriate security solutions should be developed and maintained to protect data security. The future of cloud-based eHealth services will be the integration of file-based and cloud-based applications that integrate a computer-based hybrid IT solution that measures the flexibility and scalability associated with cloud management and healthcare data security. This review highlights a comprehensive study of existing cloud-based eHealth solutions that incorporate cryptographic and non-cryptographic methods for protecting the privacy and security of digital data.
Acknowledgements
We thank the anonymous reviewers for their valuable comments and suggestions, which helped us to improve the content of our paper.
Author contributions
R.S. and Z.A.Z.; methodology: R.S.; data curation: R.S.; resources: R.S.; writing—original draft preparation: R.S.; writing—review and editing: R.S. and Z.A.Z.; supervision. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of interest
The authors declare no conflict of interest.
References
- ↑ Kruse, C.S.; Mileski, M.; Vijaykumar, A.G. et al. (2017). "Impact of Electronic Health Records on Long-Term Care Facilities: Systematic Review". JMIR Medical Informatics 5 (3): e35. doi:10.2196/medinform.7958. PMC PMC5640822. PMID 28963091. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5640822.
- ↑ Butpheng, C.; Yeh, K.-H.; Xiong, H. (2020). "Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review". Symmetry 12 (7): 1191. doi:10.3390/sym12071191.
- ↑ Ismail, L.; Materwala, H. (2020). "Blockchain Paradigm for Healthcare: Performance Evaluation". Symmetry 12 (8): 1200. doi:10.3390/sym12081200.
- ↑ Malluhi, Q.; Tran, V.D.; Trinh, V.C (2020). "Decentralized Broadcast Encryption Schemes with Constant Size Ciphertext and Fast Decryption". Symmetry 12 (6): 969. doi:10.3390/sym12060969.
- ↑ Hassen, O.A.; Abdulhissein, A.A.; Darwish, S.M. et al. (2020). "Towards a Secure Signature Scheme Based on Multimodal Biometric Technology: Application for IOT Blockchain Network". Symmetry 12 (10): 1699. doi:10.3390/sym12101699.
- ↑ Abdulghani, H.A.; Nijdam, N.A.; Collen, A. et al. (2019). "A Study on Security and Privacy Guidelines, Countermeasures, Threats: IoT Data at Rest Perspective". Symmetry 11 (6): 774. doi:10.3390/sym11060774.
- ↑ Kang, J.; Chung, H.; Lee, J. et al. (2016). "The Design and Analysis of a Secure Personal Healthcare System Based on Certificates". Symmetry 8 (11): 129. doi:10.3390/sym8110129.
- ↑ 8.0 8.1 Griebel, L.; Prokosch, H.-U.; Köpcke, F. et al. (2015). "A scoping review of cloud computing in healthcare". BMC Medical Informatics and Decision Making 15: 17. doi:10.1186/s12911-015-0145-7.
- ↑ 9.0 9.1 Venčkauskas, A.; Štuikys, V.; Toldinas, J. et al. (2016). "A Model-Driven Framework to Develop Personalized Health Monitoring". Symmetry 8 (7): 65. doi:10.3390/sym8070065.
- ↑ 10.0 10.1 Khan, M.A. (2020). "An IoT Framework for Heart Disease Prediction Based on MDCNN Classifier". IEEE Access 8: 34717–27. doi:10.1109/ACCESS.2020.2974687.
- ↑ 11.0 11.1 Yang, M.; Hara-Azumi, Y. (2020). "Implementation of Lightweight eHealth Applications on a Low-Power Embedded Processor". IEEE Access 8: 121724–32. doi:10.1109/ACCESS.2020.3006901.
- ↑ Guo, L.; Li, Z.; Yau, W.-C. et al. (2020). "A Decryptable Attribute-Based Keyword Search Scheme on eHealth Cloud in Internet of Things Platforms". IEEE Access 8: 26107–18. doi:10.1109/ACCESS.2020.2971088.
- ↑ Edemacu, K.; Park, H.K.; Jang, B. et al. (2019). "Privacy Provision in Collaborative Ehealth With Attribute-Based Encryption: Survey, Challenges and Future Directions". IEEE Access 7: 89614—89636. doi:10.1109/ACCESS.2019.2925390.
- ↑ Ma, H.; Xie, Y.; Wang, J. et al. (2019). "Revocable Attribute-Based Encryption Scheme With Efficient Deduplication for Ehealth Systems". IEEE Access 7: 89205–17. doi:10.1109/ACCESS.2019.2926627.
- ↑ Caiza, J.C.; Martin, Y.-S.; Guamán, D.S. et al. (2019). "Reusable Elements for the Systematic Design of Privacy-Friendly Information Systems: A Mapping Study". IEEE Access 7: 66512–35. doi:10.1109/ACCESS.2019.2918003.
- ↑ 16.0 16.1 Chenthara, S.; Ahmed, K.; Wang, H. et al. (2019). "Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing". IEEE Access 7: 74361–82. doi:10.1109/ACCESS.2019.2919982.
- ↑ Razaque, A.; Amsaad, F.; Khan, M.J. et al. (2019). "Survey: Cybersecurity Vulnerabilities, Attacks and Solutions in the Medical Domain". IEEE Access 7: 168774–97. doi:10.1109/ACCESS.2019.2950849.
- ↑ 18.0 18.1 Kim, J.W.; Edemacy, K.; Jang, B. (2019). "MPPDS: Multilevel Privacy-Preserving Data Sharing in a Collaborative eHealth System". IEEE Access 7: 109910–23. doi:10.1109/ACCESS.2019.2933542.
- ↑ Bouras, M.A.; Lu, Q.; Zhang, F.; et al. (2020). "Distributed Ledger Technology for eHealth Identity Privacy: State of The Art and Future Perspective". Sensors 20 (2): 483. doi:10.3390/s20020483. PMC PMC7013398. PMID 31952172. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7013398.
- ↑ Seol, K.; Kim, Y.-G.; Lee, E. et al. (2018). "Privacy-Preserving Attribute-Based Access Control Model for XML-Based Electronic Health Record System". IEEE Access 6: 9114—28. doi:10.1109/ACCESS.2018.2800288.
- ↑ Zhu, L.; Zhang, C.; Xu, C. et al. (2018). "An Efficient and Privacy-Preserving Biometric Identification Scheme in Cloud Computing". IEEE Access 6: 19025–33. doi:10.1109/ACCESS.2018.2819166.
- ↑ Qadir, J.; Mujeeb-U-Rahman, M.; Rehmani, M.H. et al. (2017). "IEEE Access Special Section Editorial: Health Informatics for the Developing World". IEEE Access 5: 27818–23. doi:10.1109/ACCESS.2017.2783118.
- ↑ Yeh, K.-H. (2016). "A Secure IoT-Based Healthcare System With Body Sensor Networks". IEEE Access 4: 10288–99. doi:10.1109/ACCESS.2016.2638038.
- ↑ Islam, S.M.R.; Kwak, D.; Kabir, H. et al. (2015). "The Internet of Things for Health Care: A Comprehensive Survey". IEEE Access 3: 678–708. doi:10.1109/ACCESS.2015.2437951.
- ↑ Tahir, A.; Chen, F.; Khan, H.U. et al. (2020). "A Systematic Review on Cloud Storage Mechanisms Concerning e-Healthcare Systems". Sensors 20 (18): 5392. doi:10.3390/s20185392. PMC PMC7570508. PMID 32967094. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7570508.
- ↑ Vilela, P.H.; Rodrigues, J.J.P.C.; Righi, R.da R. et al. (2020). "Looking at Fog Computing for E-Health through the Lens of Deployment Challenges and Applications". Sensors 20 (9): 2553. doi:10.3390/s20092553.
- ↑ Haque, R.U.; Hasan, A.S.M.T.; Jiang, Q. et al. (2020). "Privacy-Preserving K-Nearest Neighbors Training over Blockchain-Based Encrypted Health Data". Electronics 9 (12): 2096. doi:10.3390/electronics9122096.
- ↑ Stamatellis, C.; Papadopoulos, P.; Pitropakis, N. et al. (2020). "A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric". Sensors 20 (22): 6587. doi:10.3390/s20226587. PMC PMC7698751. PMID 33218022. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7698751.
- ↑ Yaqoob, T.; Abbas, H.; Atiquzzaman, M. et al. (2019). "Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review". IEEE Communications Surveys & Tutorials 21 (4): 3723—68. doi:10.1109/COMST.2019.2914094.
- ↑ Seh, A.H.; Zarour, M.; Alenezi, M. et al. (2020). "Healthcare Data Breaches: Insights and Implications". Healthcare 8 (2): 133. doi:10.3390/healthcare8020133.
- ↑ Liu, H.; Crespo, R.G.; Martinez, O.S. (2020). "Enhancing Privacy and Data Security across Healthcare Applications Using Blockchain and Distributed Ledger Concepts". Healthcare 8 (3): 243. doi:10.3390/healthcare8030243.
- ↑ Dang, L.M.; Piran, M.J.; Han, D. et al. (2019). "A Survey on Internet of Things and Cloud Computing for Healthcare". Electronics 8 (7): 768. doi:10.3390/electronics8070768.
- ↑ Huang, Q.; Yue, W.; He, Y. et al. (2018). "Secure Identity-Based Data Sharing and Profile Matching for Mobile Healthcare Social Networks in Cloud Computing". IEEE Access 6: 36584–94. doi:10.1109/ACCESS.2018.2852784.
- ↑ Celesti, A.; Fazio, M.; Márquez, F.G. et al. (2019). "How to Develop IoT Cloud e-Health Systems Based on FIWARE: A Lesson Learnt". Journal of Sensor and Actuator Networks 8 (1): 7. doi:10.3390/jsan8010007.
- ↑ Schiza, E.C.; Kyprianou, T.C.; Petkov, N. et al. (2019). "Proposal for an eHealth Based Ecosystem Serving National Healthcare". IEEE Journal of Biomedical and Health Informatics 23 (3): 1346–57. doi:10.1109/JBHI.2018.2834230. PMID 29993757.
- ↑ Lin, H.-Y.; Jiang, Y.-R. (2021). "A Multi-User Ciphertext Policy Attribute-Based Encryption Scheme with Keyword Search for Medical Cloud System". Applied Sciences 11 (1): 63. doi:10.3390/app11010063.
- ↑ Mehmood, Z.; Ghani, A.; Chen, G. et al. (2019). "Authentication and Secure Key Management in E-Health Services: A Robust and Efficient Protocol Using Biometrics". IEEE Access 7: 113385–97. doi:10.1109/ACCESS.2019.2935313.
- ↑ 38.0 38.1 Khezr, S.; Moniruzzaman, M.; Yassine, A. et al. (2019). "Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research". Applied Sciences 9 (9): 1736. doi:10.3390/app9091736.
- ↑ Li, H.; Yang, Y.; Dai, Y. et al. (2017). "Achieving Secure and Efficient Dynamic Searchable Symmetric Encryption over Medical Cloud Data". IEEE Transactions on Cloud Computing 8 (2): 484–94. doi:10.1109/TCC.2017.2769645.
- ↑ Zhang, R.; Xue, R.; Liu, L. (2017). "Searchable Encryption for Healthcare Clouds: A Survey". IEEE Transactions on Services Computing 11 (6): 978–96. doi:10.1109/TSC.2017.2762296.
- ↑ Edemacu, K.; Jang, B.; Kim, J.W. (2020). "Collaborative Ehealth Privacy and Security: An Access Control With Attribute Revocation Based on OBDD Access Structure". IEEE Journal of Biomedical and Health Informatics 24 (10): 2960-2972. doi:10.1109/JBHI.2020.2973713. PMID 32071017.
- ↑ Tong, Y.; Sun, J.; Chow, S.S.M. et al. (2014). "Cloud-assisted mobile-access of health data with privacy and auditability". IEEE Journal of Biomedical and Health Informatics 18 (2): 419–29. doi:10.1109/JBHI.2013.2294932. PMID 24608047.
- ↑ Kurdi, H.; Alsalmah, S.; Alatawi, A. et al. (2019). "HealthyBroker: A Trustworthy Blockchain-Based Multi-Cloud Broker for Patient-Centered eHealth Services". Electronics 8 (6): 602. doi:10.3390/electronics8060602.
- ↑ Zhang, Y.; Xu, C.; Li, H. et al. (2018). "HealthDep: An Efficient and Secure Deduplication Scheme for Cloud-Assisted eHealth Systems". IEEE Transactions on Industrial Informatics 14 (9): 4101–12. doi:10.1109/TII.2018.2832251.
- ↑ Yeh, L.-Y.; Chiang, P.-Y.; Tsai, Y.-L. et al. (2018). "Cloud-Based Fine-Grained Health Information Access Control Framework for Lightweight IoT Devices with Dynamic Auditing and Attribute Revocation". IEEE Transactions on Cloud Computing 6 (2): 532–44. doi:10.1109/TCC.2015.2485199.
- ↑ Avila, K.; Sanartin, P.; Jabba, D. et al. (2017). "Applications Based on Service-Oriented Architecture (SOA) in the Field of Home Healthcare". Sensors 17 (8): 1703. doi:10.3390/s17081703.
- ↑ Guo, L.; Zhang, C.; Sun, J. et al. (2014). "A Privacy-Preserving Attribute-Based Authentication System for Mobile Health Networks". IEEE Transactions on Mobile Computing 13 (9): 1927–41. doi:10.1109/TMC.2013.84.
- ↑ Liu, Y.; Zhang, Y.; Ling, J. et al. (2018). "Secure and fine-grained access control on e-healthcare records in mobile cloud computing". Future Generation Computer Systems 78 (3): 1020–26. doi:10.1016/j.future.2016.12.027.
- ↑ Elgendi, M.; Al-Ali, A.; Mohamed, A. et al. (2018). "Improving Remote Health Monitoring: A Low-Complexity ECG Compression Approach". Diagnostics 8 (1): 10. doi:10.3390/diagnostics8010010.
- ↑ Liagkou, V.; Kavvadas, V.; Chronopoulos, S.K. et al. (2019). "Attack Detection for Healthcare Monitoring Systems Using Mechanical Learning in Virtual Private Networks over Optical Transport Layer Architecture". Computation 7 (2): 24. doi:10.3390/computation7020024.
- ↑ AbuKhousa, E.; Mohamed, N.; Al-Jaroodi, J. (2012). "e-Health Cloud: Opportunities and Challenges". Future Internet 4 (3): 621–45. doi:10.3390/fi4030621.
- ↑ Sahmim, S.; Gharsellaoui, H. (2017). "Privacy and Security in Internet-based Computing: Cloud Computing, Internet of Things, Cloud of Things: A review". Procedia Computer Science 112: 1516–22. doi:10.1016/j.procs.2017.08.050.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation. However, extensive grammar, punctuation, and idea organization and clean up was required to improve the readability of the original article. In some cases important information was missing from the references, and that information was added. The original citation seven (Huh 2018) was omitted in this version as it appeared to have no connection to the topic cited. A paragraph appearing in the original introduction involving "mists" and service level agreements also had no bearing to the paper and appears to have been accidentally included in the original; it is omitted for this version. The original includes material from Azeez and Van der Vyver 2019 in the "Proposed solutions for security in cloud-based eHealth systems" section; that content was omitted for this version as it appears inadvertent or plagiarized. Finally, the Discussion in the original is a complete disaster, referencing numerous articles that aren't even discussed or cited (e.g., a mention of Rahmani et al.'s UT-Gate, as well as more almost-plagiarized content from Azeez and Van der Vyver 2019). The discussion was completely removed for this version as it too appears to be inadvertent or plagiarized content.