Difference between revisions of "Journal:Understanding cybersecurity frameworks and information security standards: A review and comprehensive overview"
Shawndouglas (talk | contribs) (Saving and adding more.) |
Shawndouglas (talk | contribs) (Saving and adding more.) |
||
| Line 75: | Line 75: | ||
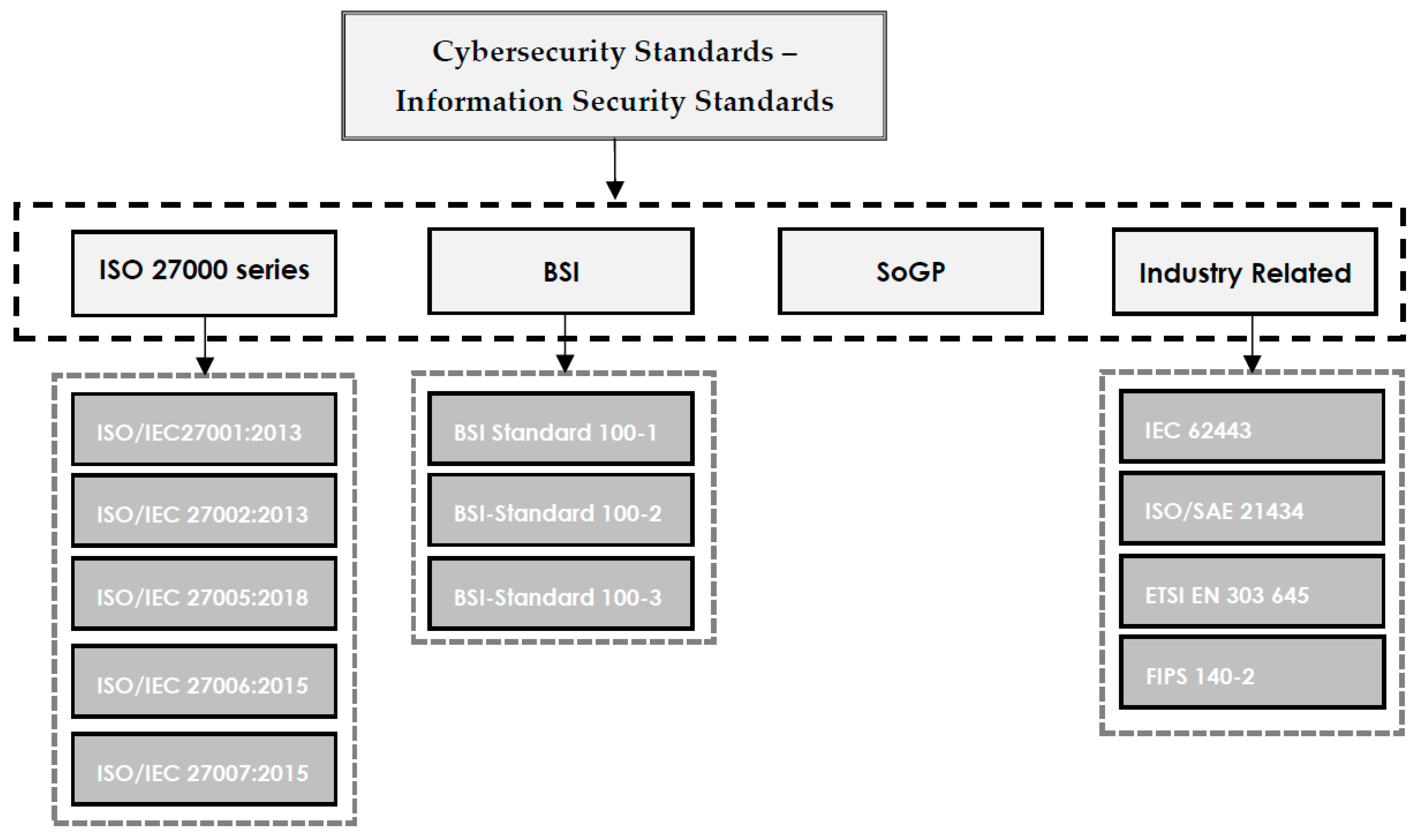
Written cybersecurity standard documents describe requirements to be respected by the organization and are easy to be controlled by stakeholders or relevant auditors. However, standards do not include how to achieve the standard requirements. The most popular and frequently used cybersecurity standards, referred to in this paper, are shown in Figure 1. It is important to note that cybersecurity frameworks may not be limited to what is presented in the scope of this study, since new frameworks are constantly being published based on demands. In a general classification, the ISO 27000 series, BSI, and SoGP are provided. Additionally, some standards that are common in industry are presented in the "Industry Related" category. | Written cybersecurity standard documents describe requirements to be respected by the organization and are easy to be controlled by stakeholders or relevant auditors. However, standards do not include how to achieve the standard requirements. The most popular and frequently used cybersecurity standards, referred to in this paper, are shown in Figure 1. It is important to note that cybersecurity frameworks may not be limited to what is presented in the scope of this study, since new frameworks are constantly being published based on demands. In a general classification, the ISO 27000 series, BSI, and SoGP are provided. Additionally, some standards that are common in industry are presented in the "Industry Related" category. | ||
[[File:Fig1 Taherdoost Electronics22 11-14.png|800px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 1''' Cybersecurity and information security standards.</blockquote> | |||
|- | |||
|} | |||
|} | |||
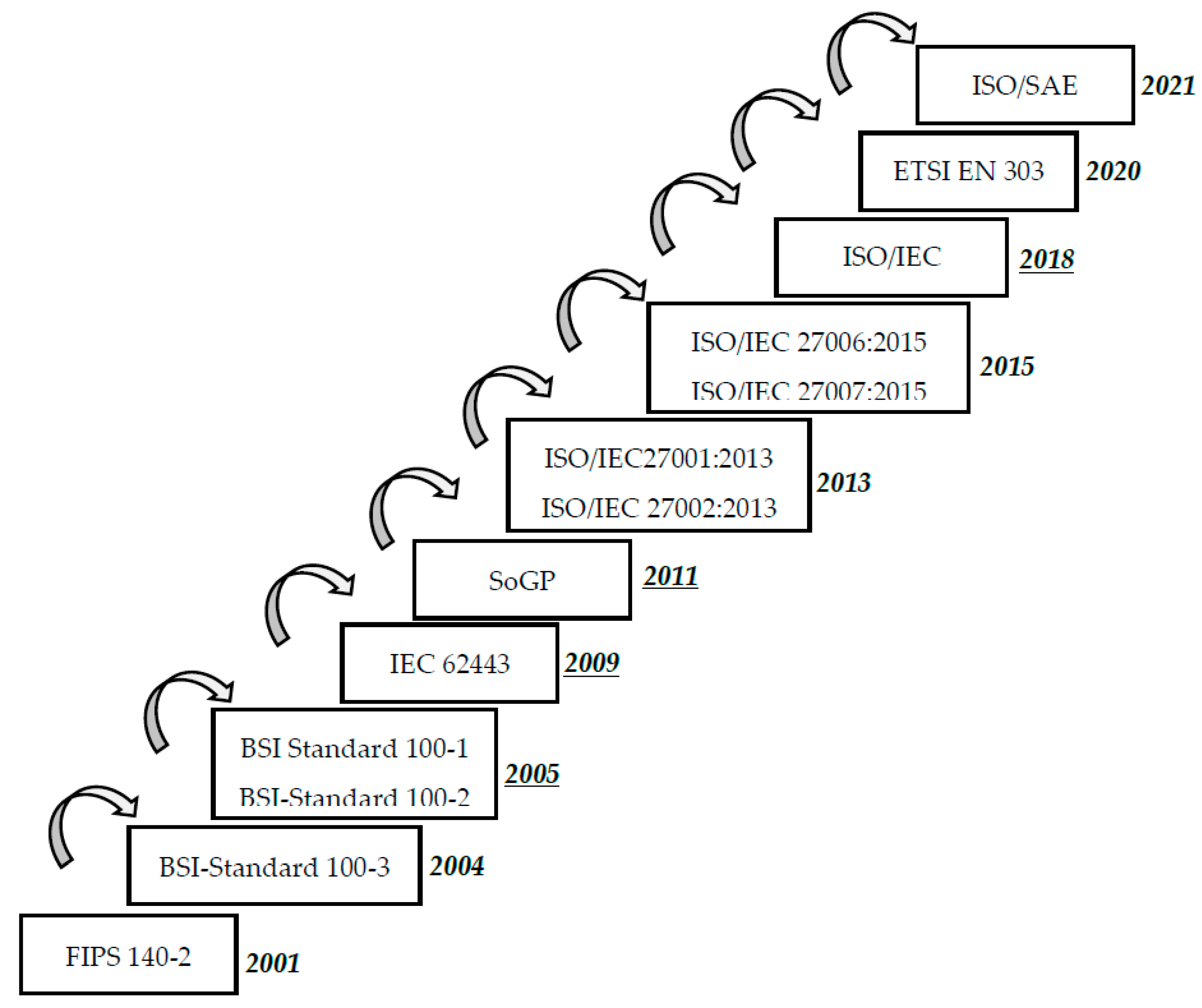
The evolution of cybersecurity standards over time is represented in Figure 2. | |||
[[File:Fig2 Taherdoost Electronics22 11-14.png|800px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 2''' Timeline of cybersecurity standards evolution.</blockquote> | |||
|- | |||
|} | |||
|} | |||
In the following subsections, the most popular cybersecurity standards—including the ISO 27000 series, SoGP, and BSI—are described to provide an overview and facilitate the process of decision-making. | |||
===ISO/IEC 27000 standards=== | |||
The ISO/IEC 27000 series of standards concentrates on security in information systems management (ISM). [15] The family of ISO/IEC 27000 standards was initially recognized as BS7799 and then introduced as ISO standards as soon as the ISO added it to the information security management system (ISMS) standards. [29] Methods and practices to ensure effective implementation of information security in an organization are described in detail in ISO 27001, focusing on providing a secure and trustable exchange of data and communication channels. The main consideration of ISO 27001 in accomplishing managerial and organizational objectives and sub-objectives is through stressing the imporatance of risk management approaches. However, the ISO 27000 series has not been shown to successfully work as a complete information systems management (ISM) solution to be integrated into larger systems. ISO 27001, the first in the series of ISO/IEC 27000 standards, dates back to 2005. However, four standards, including 27001, 27002, 27005, and 27006, are currently published and widely used in organizations. [30] | |||
====ISO/IEC 27001:2013==== | |||
ISO/IEC 27001:2013 is an internationally recognized standard that determines requirements to implement a certified ISMS for a business through seven key elements. [10] These steps include specifications for installation, performance, operation, controlling and monitoring, review, maintenance, and improvement of the system. General requirements for the treatment and assessment of risks that exist in the information system of the organizations are also included, regardless of the size, type, and nature of the business. ISO/IEC 27001 is commonly used along with ISO/IEC 27002, which clarifies security control objectives and recommendations, since it does not list specific security controls. Employment of ISO/IEC 27001 helps organizations to manage and protect the valuable information of employees and clients, manage information risks, and protect and develop their brands. [31] (Note that since the original publishing of this journal article, the standard was updated, in October 2022.) | |||
====ISO/IEC 27002:2013==== | |||
ISO/IEC 27002:2013 is the code of practice for information security controls that lists a structured series of information security controls to comply with ISO/IEC 27001. However, security controls that are not specifically mentioned in this list are not mandatory to be employed by organizations. Best practice recommendations to be used by responsible individuals when they try to implement information security management are provided in ISO/IEC 27002. [32] This includes managing assets in an organization, securing human resources, managing operations and communications, securing environmental and physical aspects, managing business continuity, and managing compliance and information security incident areas. [25] (Note that since the original publishing of this journal article, the standard was updated, in February 2022.) | |||
====ISO/IEC 27005:2018==== | |||
Guidelines for risk-based implementation of cybersecurity risk management are provided in ISO/IEC 27005:2018. The standard supports concepts and requirements that are specifically listed in ISO/IEC 27001. To completely understand ISO/IEC 27005, organizations need to gain knowledge about the processes and concepts of ISO/IEC 27001 and ISO/IEC 27002. ISO/IEC 27005 can be applicable to those implementing a satisfactory risk-based information system in organizations of different sizes and sectors. [33] ISO/IEC 27005 employs an information risk management process that consists of seven main elements, including installation of context, assessing risk, treating risk, accepting risk, communicating risk, consulting risk, as well as monitoring risk and reviewing risk. [25] (Note that since the original publishing of this journal article, the standard was updated, in October 2022.) | |||
====ISO/IEC 27006:2015==== | |||
The main purpose of ISO/IEC 27006 is to determine formal processes and requirements that should be respected by third-party bodies that provide information security auditing and certifying services for other organizations. Conforming to ISO/IEC 27006 helps bodies to be recognized as trustable and reliable organizations operating ISMS. [10] | |||
====Other ISO/IEC standards==== | |||
Other cybersecurity and information security standards put forth by the ISO/IEC JTC 1/SC 27 technical committee include [25]: | |||
* ISO/IEC 27000:2018 ''Information technology — Security techniques — Information security management systems — Overview and vocabulary'' | |||
* ISO/IEC 27003:2017 ''Information technology — Security techniques — Information security management systems — Guidance'' | |||
* ISO/IEC 27004:2016 ''Information technology — Security techniques — Information security management — Monitoring, measurement, analysis and evaluation'' | |||
* ISO/IEC 27007:2020 ''Information security, cybersecurity and privacy protection — Guidelines for information security management systems auditing'' | |||
* ISO/IEC TS 27008:2019 ''Information technology — Security techniques — Guidelines for the assessment of information security controls'' | |||
* ISO/IEC 27009:2020 ''Information security, cybersecurity and privacy protection — Sector-specific application of ISO/IEC 27001 — Requirements'' | |||
* ISO/IEC 27011:2016 ''Information technology — Security techniques — Code of practice for Information security controls based on ISO/IEC 27002 for telecommunications organizations'' | |||
* ISO/IEC 27013:2021 ''Information security, cybersecurity and privacy protection — Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1'' | |||
* ISO/IEC 27014:2020 ''Information security, cybersecurity and privacy protection — Governance of information security'' | |||
* ISO/IEC TR 27016:2014 ''Information technology — Security techniques — Information security management — Organizational economics'' | |||
* ISO/IEC 27017:2015 ''Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services'' | |||
* ISO/IEC 27018:2019 ''Information technology — Security techniques — Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors'' | |||
* ISO/IEC 27019:2017 ''Information technology — Security techniques — Information security controls for the energy utility industry'' | |||
Revision as of 15:13, 15 March 2023
| Full article title | Understanding cybersecurity frameworks and information security standards: A review and comprehensive overview |
|---|---|
| Journal | Electronics |
| Author(s) | Taherdoost, Hamed |
| Author affiliation(s) | University Canada West |
| Primary contact | Email: hamed dot taherdoost at gmail dot com |
| Year published | 2022 |
| Volume and issue | 11(14) |
| Article # | 2181 |
| DOI | 10.3390/electronics11142181 |
| ISSN | 2079-9292 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2079-9292/11/14/2181 |
| Download | https://www.mdpi.com/2079-9292/11/14/2181/pdf (PDF) |
|
|
This article should be considered a work in progress and incomplete. Consider this article incomplete until this notice is removed. |
Abstract
Businesses are reliant on data to survive in the competitive market, and data is constantly in danger of loss or theft. Loss of valuable data leads to negative consequences for both individuals and organizations. Cybersecurity is the process of protecting sensitive data from damage or theft. To successfully achieve the objectives of implementing cybersecurity at different levels, a range of procedures and standards should be followed. Cybersecurity standards determine the requirements that an organization should follow to achieve cybersecurity objectives and minimize the impact of cybercrimes. Cybersecurity standards demonstrate whether an information management system can meet security requirements through a range of best practices and procedures. A range of standards has been established by various organizations to be employed in information management systems of different sizes and types. However, it is challenging for businesses to adopt the standard that is the most appropriate based on their cybersecurity demands. Reviewing the experiences of other businesses in the industry helps organizations to adopt the most relevant cybersecurity standards and frameworks.
This study presents a narrative review of the most frequently used cybersecurity standards and frameworks based on 1. existing papers in the cybersecurity field and 2. applications of these cybersecurity standards and frameworks in various fields to help organizations select the cybersecurity standard or framework that best fits their cybersecurity requirements.
Keywords: cybersecurity framework, cybersecurity standard, information security framework, information security standard, cybersecurity requirements, information security requirements, narrative review
Introduction
A standard is described as an ideal condition with a minimum achievement limit. [1] It also refers to technical specifications that are required to be applied by a service facility to enable service users to acquire the maximum function, purpose, or profit from the services. [2] Many international organizations, associations, and consortia have a vital role in the development of standards. [3,4] According to Standards Australia[1], standards are represented as documents which define specifications, procedures, and guidelines, aiming to ensure safety, consistency, and reliability of products, services, and systems. Moreover, based on the provided definition by the International Organization for Standardization/International Electrotechnical Commission (ISO/IEC), standards are documents or rules made based on a general agreement and validated by a legal entity, which help to achieve optimal results, as a guideline, model, or sample, in a particular context.[2] A standard practically meets user demands, considers the limitations of technology and resources, and also meets the verification requirements. [2]
The term "standard" most commonly refers to established documents by professional bodies to be used by other organizations (i.e., technical standards, program standards), or standards of technical practice (i.e., practical cybersecurity standards).
The sets of practices or technical methods that help organizations to secure their cyber environment are referred to as cybersecurity standards. [6] Cybersecurity standards include users, network infrastructure, software, hardware, processes, and information in system storage media that can be connected to the internet. [6] The scope of cybersecurity standards is broad in that it covers security features in applications and cryptographic algorithms that mainly provide perspective toward security controls, processes, procedures, guidelines, and baselines. [7] Security experts recommend implementing cybersecurity standards as a fundamentally essential element consisting of a collection of best practices to protect organizations from cybersecurity threats and risks. [8]
The main aim of cybersecurity standards is to prevent or mitigate cyberattacks and reduce the risk of cyber threats. [9] The implementation of such standards typically benefits the adopter by saving time, decreasing costs, increasing profits, improving user awareness, minimizing risks, and offering business continuity. [7] Additionally, using standards facilitates the compliance of an organization to industry best practices and procedures and provides the opportunity to compare a security system on an international level. [10] Hence, the application of cybersecurity standards has been established in different organizations or businesses to protect assets against cyber threats. [11,12] As a result, different cybersecurity standards have been developed by various organizations to ensure that organizations of different size and nature implement appropriate measures to prevent and mitigate cyber threats. [13] However, since a considerable number of standards have been developed to cover different aspects of cybersecurity in various organizations, it may be challenging for business owners to choose the appropriate standard that is the best match for their business. [14]
This study aims to provide an overview of the most frequently used cybersecurity standards based on existing papers in the cybersecurity field, clarifying their features and applications in different industries. A wide range of cybersecurity standards and frameworks are available to ensure the protection of data in different industries; however, this review paper aims to provide a comparative concept regarding cybersecurity standards and frameworks and facilitate the selection of the most appropriate standards and frameworks. This paper can be also helpful for academic purposes to determine the direction of further studies in this field.
In the next section, an overview of the most common cybersecurity standards and frameworks is provided. Following that is a narrative literature review that is the result of extracting and analyzing 17 papers published about cybersecurity standards between 2000 to 2022, and then considering the aim of each study, the main findings of the research, as well as relevant industry and employed standards. Finally, a concluding discussion is presented that clarifies the contribution of different standards for specific purposes.
Cybersecurity standards and frameworks
Cybersecurity standards are generally classified into two main categories: information security standards and information security governance standards. [15] Information security standards and frameworks such as the ISO/IEC 27000 series, ISF SOGP, NIST 800 series, SOX, and Risk IT mainly concentrate on security concerns. Selecting the most appropriate standard or framework is a serious decision that should be made based on the requirements of the organization to examine if it adequately suits the demands of the business. In some cases, employment of a single standard does not suffice to meet the expectations of a business. Thus, managers need to examine whether they need to consider more than one standard or framework. [2]
Open standards and frameworks are easily available and optional to be employed. Thus, organizations can use some parts or all of the guidelines, as required, or use them in combination, integrated with other standards, to complement and strengthen other requirements. [16] Performance standards can be a policy or law to be complied with by certain countries. They may also be required by the responsible organization, association, or regulatory body to be complied with by the implementing organization. [17] A country or company is authorized to reject rules or standards published by others, or to develop their own proprietary standards or local regulatory standards. [18]
The effective implementation of cybersecurity standards as guidelines or techniques which include best practices to be used in business or industry is not possible without the employment of the relevant cybersecurity framework. [19,20] Cybersecurity standards explain and provide methods one by one, specify what is expected to be done to complete the process, and clarify methods to coincide with the standard; a cybersecurity framework is a general guideline that covers many components or domains that can be adopted by businesses/companies/institutions, which doesn't necessarily specify the steps that are required to be taken. [21] Satisfactory cybersecurity protection can be achieved by adopting a cybersecurity framework that describes the scope, implementation, and evaluation processes, and also provides a general structure and methodology for protecting critical digital assets. [22] In fact, organizations can refer to cybersecurity frameworks to realize guidelines in the successful implementation of cybersecurity standards to be better equipped to identify, detect, and respond to cyberattacks. [23]
Cybersecurity frameworks are flexible and can provide users with the freedom to choose some parts or the whole model, methods, or technical practices, offering general and adoptable guidelines, as well as offering suggestions to be applied within the organization. [24] Implementation costs can be reduced as a result of the flexibility of cybersecurity frameworks. This can be effective to protect the infrastructure against cyber threats and secure critical sectors in the nation and economy. Therefore, cybersecurity frameworks have been developed by academic institutions, international organizations, countries, and corporations to ensure cyber resilience. [25] Businesses that seek to successfully implement cybersecurity standards are dependent on cybersecurity frameworks to harmonize policy, business, and technological approaches that are effective to mitigate cybersecurity issues and address cyber risks. [26] Thus, to ensure the protection of data and the infrastructure in organizations, businesses, and governments, cybersecurity standards and frameworks are required. [27]
The difference between a standard and a framework is summarized in Table 1.
| ||||||
Cybersecurity and information security standards
Cybersecurity standards, as key parts of IT governance, are consulted to ensure that an organization is following its policies and strategy in cybersecurity. [3] Therefore, by relying on cybersecurity standards, an organization can turn its cybersecurity policies into measurable actions. Cybersecurity standards clarify functional and assurance steps that should be taken to achieve the objectives of the organization in terms of cybersecurity. It may seem costly for a business to invest in the implementation of cybersecurity standards; however, the confidence and trust that it brings are more beneficial for the organization. [28]
Written cybersecurity standard documents describe requirements to be respected by the organization and are easy to be controlled by stakeholders or relevant auditors. However, standards do not include how to achieve the standard requirements. The most popular and frequently used cybersecurity standards, referred to in this paper, are shown in Figure 1. It is important to note that cybersecurity frameworks may not be limited to what is presented in the scope of this study, since new frameworks are constantly being published based on demands. In a general classification, the ISO 27000 series, BSI, and SoGP are provided. Additionally, some standards that are common in industry are presented in the "Industry Related" category.
|
The evolution of cybersecurity standards over time is represented in Figure 2.
|
In the following subsections, the most popular cybersecurity standards—including the ISO 27000 series, SoGP, and BSI—are described to provide an overview and facilitate the process of decision-making.
ISO/IEC 27000 standards
The ISO/IEC 27000 series of standards concentrates on security in information systems management (ISM). [15] The family of ISO/IEC 27000 standards was initially recognized as BS7799 and then introduced as ISO standards as soon as the ISO added it to the information security management system (ISMS) standards. [29] Methods and practices to ensure effective implementation of information security in an organization are described in detail in ISO 27001, focusing on providing a secure and trustable exchange of data and communication channels. The main consideration of ISO 27001 in accomplishing managerial and organizational objectives and sub-objectives is through stressing the imporatance of risk management approaches. However, the ISO 27000 series has not been shown to successfully work as a complete information systems management (ISM) solution to be integrated into larger systems. ISO 27001, the first in the series of ISO/IEC 27000 standards, dates back to 2005. However, four standards, including 27001, 27002, 27005, and 27006, are currently published and widely used in organizations. [30]
ISO/IEC 27001:2013
ISO/IEC 27001:2013 is an internationally recognized standard that determines requirements to implement a certified ISMS for a business through seven key elements. [10] These steps include specifications for installation, performance, operation, controlling and monitoring, review, maintenance, and improvement of the system. General requirements for the treatment and assessment of risks that exist in the information system of the organizations are also included, regardless of the size, type, and nature of the business. ISO/IEC 27001 is commonly used along with ISO/IEC 27002, which clarifies security control objectives and recommendations, since it does not list specific security controls. Employment of ISO/IEC 27001 helps organizations to manage and protect the valuable information of employees and clients, manage information risks, and protect and develop their brands. [31] (Note that since the original publishing of this journal article, the standard was updated, in October 2022.)
ISO/IEC 27002:2013
ISO/IEC 27002:2013 is the code of practice for information security controls that lists a structured series of information security controls to comply with ISO/IEC 27001. However, security controls that are not specifically mentioned in this list are not mandatory to be employed by organizations. Best practice recommendations to be used by responsible individuals when they try to implement information security management are provided in ISO/IEC 27002. [32] This includes managing assets in an organization, securing human resources, managing operations and communications, securing environmental and physical aspects, managing business continuity, and managing compliance and information security incident areas. [25] (Note that since the original publishing of this journal article, the standard was updated, in February 2022.)
ISO/IEC 27005:2018
Guidelines for risk-based implementation of cybersecurity risk management are provided in ISO/IEC 27005:2018. The standard supports concepts and requirements that are specifically listed in ISO/IEC 27001. To completely understand ISO/IEC 27005, organizations need to gain knowledge about the processes and concepts of ISO/IEC 27001 and ISO/IEC 27002. ISO/IEC 27005 can be applicable to those implementing a satisfactory risk-based information system in organizations of different sizes and sectors. [33] ISO/IEC 27005 employs an information risk management process that consists of seven main elements, including installation of context, assessing risk, treating risk, accepting risk, communicating risk, consulting risk, as well as monitoring risk and reviewing risk. [25] (Note that since the original publishing of this journal article, the standard was updated, in October 2022.)
ISO/IEC 27006:2015
The main purpose of ISO/IEC 27006 is to determine formal processes and requirements that should be respected by third-party bodies that provide information security auditing and certifying services for other organizations. Conforming to ISO/IEC 27006 helps bodies to be recognized as trustable and reliable organizations operating ISMS. [10]
Other ISO/IEC standards
Other cybersecurity and information security standards put forth by the ISO/IEC JTC 1/SC 27 technical committee include [25]:
- ISO/IEC 27000:2018 Information technology — Security techniques — Information security management systems — Overview and vocabulary
- ISO/IEC 27003:2017 Information technology — Security techniques — Information security management systems — Guidance
- ISO/IEC 27004:2016 Information technology — Security techniques — Information security management — Monitoring, measurement, analysis and evaluation
- ISO/IEC 27007:2020 Information security, cybersecurity and privacy protection — Guidelines for information security management systems auditing
- ISO/IEC TS 27008:2019 Information technology — Security techniques — Guidelines for the assessment of information security controls
- ISO/IEC 27009:2020 Information security, cybersecurity and privacy protection — Sector-specific application of ISO/IEC 27001 — Requirements
- ISO/IEC 27011:2016 Information technology — Security techniques — Code of practice for Information security controls based on ISO/IEC 27002 for telecommunications organizations
- ISO/IEC 27013:2021 Information security, cybersecurity and privacy protection — Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1
- ISO/IEC 27014:2020 Information security, cybersecurity and privacy protection — Governance of information security
- ISO/IEC TR 27016:2014 Information technology — Security techniques — Information security management — Organizational economics
- ISO/IEC 27017:2015 Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services
- ISO/IEC 27018:2019 Information technology — Security techniques — Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
- ISO/IEC 27019:2017 Information technology — Security techniques — Information security controls for the energy utility industry
References
- ↑ "What is a standard?". Standards Australia. 2022. https://www.standards.org.au/standards-development/what-is-standard. Retrieved 01 February 2022.
- ↑ "ISO/IEC Directives, Part 2: Rules for the structure and drafting of International Standards" (PDF). International Organization for Standardization, International Electrotechnical Commission. 2011. https://boss.cen.eu/media/yypjl3mn/iso_iec_directives_part2.pdf.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added.