Journal:Cybersecurity and privacy risk assessment of point-of-care systems in healthcare: A use case approach
| Full article title | Cybersecurity and privacy risk assessment of point-of-care systems in healthcare: A use case approach |
|---|---|
| Journal | Applied Sciences |
| Author(s) | Jofre, Marc; Navarro-Llobet, Diana; Agulló, Ramon; Puig, Jordi; Gonzalez-Granadillo, Gustavo; Zamorano, Juan M.; Romeu, Ramon |
| Author affiliation(s) | Fundació Privada Hospital Asil de Granollers, Atos Research & Innovation, Servicio Madrileño de Salud |
| Primary contact | Email: diananavarro at fphag dot org |
| Editors | Chizari, Hassan |
| Year published | 2021 |
| Volume and issue | 11(15) |
| Article # | 6699 |
| DOI | 10.3390/app11156699 |
| ISSN | 2076-3417 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2076-3417/11/15/6699/htm |
| Download | https://www.mdpi.com/2076-3417/11/15/6699/pdf (PDF) |
|
|
This article should be considered a work in progress and incomplete. Consider this article incomplete until this notice is removed. |
Abstract
Point-of-care (POC) systems are generally used in healthcare to respond rapidly and prevent critical health conditions. Hence, POC systems often handle personal health information, and, consequently, their cybersecurity and privacy requirements are of crucial importance. However, assessing these requirements is a significant task.
In this work, we propose a use-case approach to assess specifications of cybersecurity and privacy requirements of POC systems in a structured and self-contained form. Such an approach is appropriate since use cases are one of the most common means adopted by developers to derive requirements. As a result, we detail a use case approach in the framework of a real-based healthcare IT infrastructure that includes a health information system, integration engines, application servers, web services, medical devices, smartphone apps, and medical modalities (all data simulated) together with the interaction with participants. Since our use case also sustains the analysis of cybersecurity and privacy risks in different threat scenarios, it also supports decision making and the analysis of compliance considerations.
Keywords: cybersecurity, healthcare, incidents, information privacy, IT infrastructure, point-of-care, risk assessment, sensitive medical data, threats, use case
Introduction
Cybersecurity and privacy incidents are a growing threat to the healthcare industry in general, and hospitals in particular.[1] The healthcare industry has lagged behind other industries in protecting its main stakeholders (e.g., care staff and patients), and now hospitals must invest considerable capital and effort in protecting their IT systems.[2] However, moving to more protected and resilient digital infrastructures in healthcare is a challenge because hospitals are technology-saturated, complex organizations with high end-point complexity, internal politics, and regulatory pressures. Therefore, healthcare organizations of all types looking to grow and achieve their financial, quality, service, and compliance performance objectives must understand and account for the capabilities, drivers, strategies, and challenges of other ecosystems such as cybersecurity and information privacy. Hence, as cybersecurity and privacy become more of a priority for hospitals, it is essential they holistically integrate the different processes, components, and stages influencing the healthcare ecosystem.
One relevant aspect to consider regarding cybersecurity and privacy risks are healthcare point-of-care (POC) systems which have been widely used in hospitals in order to provide innovative solutions to medical professionals. POC systems provide an overview of patients’ conditions in a way that makes it easier for professionals to respond in a timely fashion and prevent critical situations. POC platforms also incorporate medical devices and applications in order to collect, process, and visualize data. As such, large amounts of data move through POC systems, including personal health information and sensitive medical data. This data is communicated across various POC systems, backend analytical platforms, user workstations, and smartphones, demonstrating that there are multiple touch points that may cause data leakages or breaches. Naturally, these platforms create and expand attack surface, which may be challenging to fully identify and address. Hospitals and care centers need to address these threats by efficiently assessing the associated risks and mitigate them with the proper cybersecurity and privacy safeguards.
POC systems can be categorized in three classes according to their usage model: (i) testing and diagnostic applications (e.g., medical devices), (ii) patient monitoring (e.g., smartphone apps), and (iii) interfacing with other devices (e.g., web-based services and integration servers).[3] Hence, considering the latter classes, some common associated threats to POC systems encompass legacy operating systems and software, lack of timely software updates and patches, medical devices not having basic security features, insecure implementation of web-services, lack of awareness of cybersecurity and privacy issues, and limited power and resources, among others.[4] Typically, these threats and risks can be exploited by several common attack methods, including cross-site scripting, Structured Query Language (SQL) or Extensible Markup Language (XML) injection, client-side attacks, malware, and denial-of-service.
Generally, risk is defined as the combined probability of an unwanted event and its level of impact. It is described as a function of the probability that a given source of threat exerts a potential vulnerability and the consequent impact of this adverse event on the organization.[5] Cybersecurity risk, also known as information technology risk, is the new management challenge of the third millennium; it affects the information and technology assets of organizations. Sardi et al. define cybersecurity risk as “operational risks to information and technology assets that have consequences affecting the confidentiality, availability, or integrity of information or information systems.”[6] In particular, a cybersecurity threat is a potential attack that exploits a vulnerability of the system to cause damage, whilst a threat scenario is a flow of events or attacks containing interactions between a malicious actor and a system to cause damage. On the other hand, privacy risk assessment, as indicated by Wagner and Boiten[7], aims to “analyze and quantify the privacy risks associated with new systems.”
Accordingly, considerable research has been devoted to eliciting and analyzing cybersecurity and privacy risk assessment.[6][7][8][9][10] However, the applicability of these approaches in the context of cybersecurity and privacy risk assessment modeling for POC systems in healthcare ecosystems shows limitations with respect to (i) their support for explicitly specifying various types of cybersecurity threats, (ii) the definition of threat scenarios, and (iii) the specification of mitigation and preventing actions (e.g., cyber hygiene) for these threats.
Moreover, the above risks have to be properly communicated and accounted in the overall operational structure of organizations. For instance, in business, financial value may be acceptable as the ultimate unit, which is used to quantify direct cost, or even reputation and human lives. However, the healthcare sector certainly does not only operate on a competitive or financial basis, and may it prefer units that more closely relate to the concept of privacy risk. Therefore, to assess the cybersecurity requirements of POC systems, it is necessary to take into consideration the characteristics of the specific service being developed and of the device types on which the service is going to be deployed.
Accordingly, use cases are one of the most common means adopted by software engineers and end-users to elicit requirements because they ease the communication between stakeholders to assess specific requirements.[11] Additionally, to achieve widespread applicability, the need for integrating cybersecurity and privacy requirements with use case modeling warrants the development of reusable templates in different applications, and in particular for healthcare applications. Systematic approaches to eliciting cybersecurity requirements based on use cases, with emphasis on description and methods guidelines have been proposed.[12] However, existing approaches lack reusable templates for misuse cases, as opposed to only well-behaving use cases.[12][13][14][15] However, with slight modifications, use cases can aid the integration of misuse case scenarios, with functional and non-functional requirements, when considering cybersecurity and privacy risk.[16]
In the direction to remediate the limitations described above, we propose a use case approach, including misuse cases, in the framework of a real healthcare IT infrastructure for POC cybersecurity and privacy risk assessment. In particular, the objectives of this work are to (i) detail a use case that sustains the specifications of cybersecurity and privacy requirements, (ii) address the above challenges by including the modelling based on the risk management capability model (RMCM), and (iii) produce an approach tailored to accounting POC in healthcare ecosystems. In this regard, the paper is organized as follows. The next section introduces the context of our use case approach and proposed scenarios, compared to the state-of-the-art, to provide the motivations behind POC systems in healthcare. The next two sections after describe the technical developments, proposed pilot plan, and risk assessment capability for POC use cases in healthcare environments, respectively. This is followed by the penultimate section, which discusses the results connected with the outcomes in several dimensions of cybersecurity and privacy risks. The final section summarizes the work, provides conclusions, and proposes future research.
Proposed use case overview
The work presented in this article has been developed as part of a European Union (E.U.) project called the Secure and Private Health Data Exchange (CUREX)[17][18][19], which is developing a software platform aimed at delivering trust-enhancing, secure, and private-by-design systems and applications for the healthcare domain. In general, CUREX delivers specific cybersecurity and privacy risk solutions based on the following set of measurable objectives:
- deliver tools for assessing cybersecurity and privacy risks associated with health data exchange,
- deliver a decision support tool for devising optimal cybersecurity and privacy safeguards,
- deliver a blockchain-based platform for enhancing trust in health data exchange,
- enhance cyber hygiene in healthcare organizations,
- demonstrate the value of the CUREX platform through proof-of-concept use cases, and
- conduct techno-economic, market, and legal analysis and propose business and application models.
In order to accomplish these objectives, the project brings academic institutions, healthcare end-users, and software development companies together in a consortium to enhance the pool of available resources with partners and competitors to leverage technology development with high impact. Therefore, in conjunction with optimal recommended safeguards, CUREX delivers targeted measures for raising the cyber hygiene of healthcare organizations through the recommendation of strategies and methodologies for training and raising awareness activities, targeted towards healthcare employees (administration, medical, and IT personnel) on cybersecurity and privacy risks incurred during data exchange.[20] Training will involve the development of cybersecurity defending skills, e.g., empowering social engineering defenses.[21] In this way, healthcare employees will feel more confident in handling and exchanging sensitive data and improve their capabilities to perform their daily professional tasks effectively and in a secure fashion.
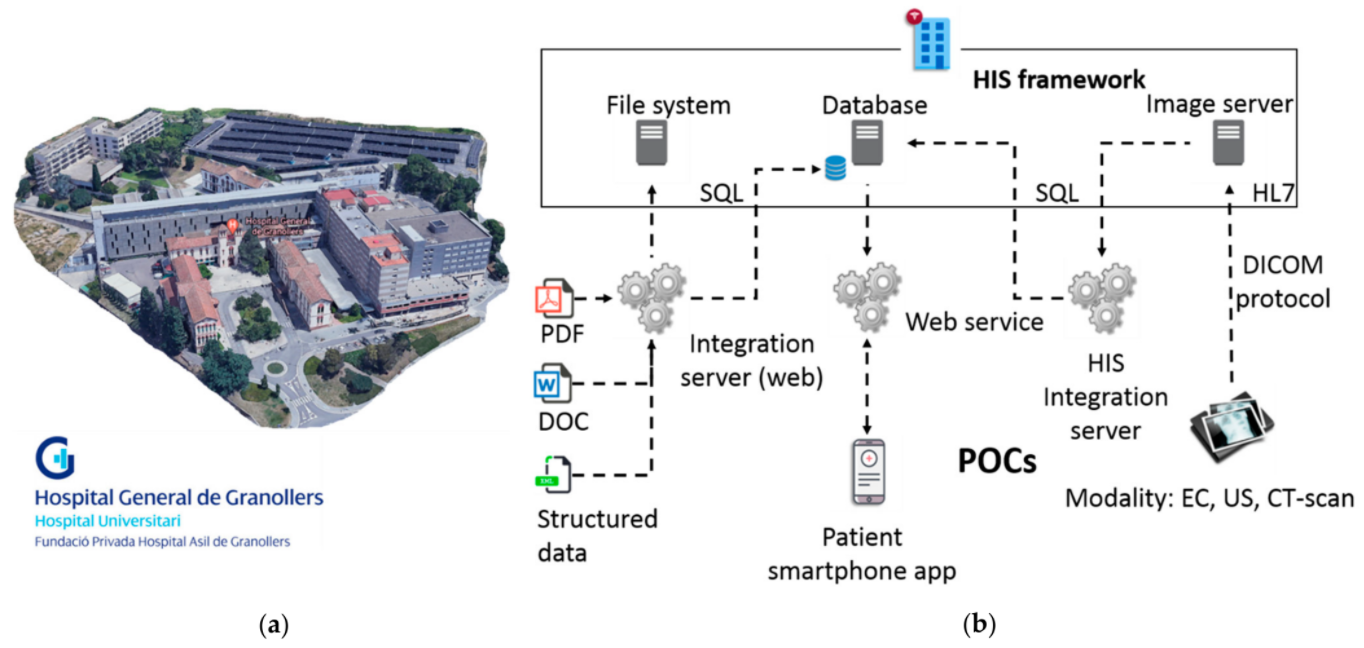
Particularly, as elucidated in the previous section, we will center this work in the development of a use case (also with misuse case extensions) to assess the cybersecurity and privacy risks in POC systems, together with remediation actions based on cyber hygiene recommendations, for different target groups of healthcare professionals at Fundació Privada Hospital Asil de Granollers (FPHAG) hospital. Contextualizing, FPHAG is a health and healthcare provider center of the public integral health system of Catalonia (SISCAT) of the Catalan health system (described in Figure 1a). The hospital provides healthcare assistance both for acute and non-acute patients, and it is the reference hospital of the territories comprising the area known as Vallès Oriental (Barcelona), serving a population of around 400,000 people with a total of 340 beds.
|
In the described context, considering data from August 2019, FPHAG’s information network infrastructure was subject to more than 6,000 different malware and intrusion attacks during a period of a year. Malware attack incidents were further classified as 205 viruses, 500 spyware, 189 adware, and 2,490 botnet attacks, whereas intrusion attack incidents’ risk levels were classified as 19 critical, 8 severe, 1,876 average, and 718 as low intensity levels. All the attacks were blocked or handled by the firewall. The latter statistics, all with positive outcome, are of relevance and effectively point out that correct infrastructure protection and IT best practices are in place at FPHAG.
While the FPHAG dealt with purely external attacks (blocked by the firewall), it's important to note that internal attacks are also very valuable to assess in a use case approach; while they are less frequent, they can produce a catastrophic outcome. Therefore, a complete independent infrastructure similar to the real IT infrastructure of the hospital has been designed and develop at FPHAG, to work with these potential attacks in a use case approach, to assess requirements for testing and improving the CUREX platform solution, as shown in Figure 1b, above. Accordingly, the developed experimental IT infrastructure is composed of:
- a health information system framework, containing file systems, a database, and an image server;
- a web integration server and services; and
- three different groups of POC systems: files of clinical history stored in the system as pdf, doc and structured data files, a patient smartphone app, and medical devices consisting of an electrocardiogram (EC), an ultrasound machine, and a CT-scan modality simulator (emulated medical device).
All the personal and health data generated and stored with the different components is simulated, hence no real data from patients has been used.
With the above-described points, the scope of the proposed use case in this work assumes the following situation:
The hospital IT department has raised concerns about the cybersecurity issues that may emerge from the operation and the communication of the clinical data handled with POC systems. Indeed, since the data contains highly sensitive personal information, it must be ensured that the hospitals’ information systems are properly maintained, and any vulnerabilities are identified and patched in a timely fashion. In addition, since the hospital has the technical capability of generating data reports and exchanging them with third parties, the platform must ensure that proper cybersecurity and privacy safeguards are in place in order to protect the integrity of the data and, most importantly, patient safety. Consequently, the hospital decides to adopt the CUREX platform in order to address these issues immediately. In conjunction with optimal recommended safeguards, CUREX delivers targeted measures for raising the cyber hygiene of healthcare organizations through the recommendation of strategies and methodologies for training and raising awareness activities, targeted towards healthcare employees (administration, medical, and IT personnel) on cybersecurity and privacy risks incurred during data exchange. Training involves the development of cybersecurity defending skills, e.g., empowering social engineering defenses. In this way, healthcare employees will feel more confident in handling and exchanging sensitive data and improve their capabilities to perform their daily professional tasks effectively and in a secure fashion.
Generally, the use case approach scope presented in this work is always with respect to POC systems' cybersecurity and privacy management, which help hospitals and care centers mitigate these risks. This becomes even more crucial when the POC systems’ data needs to be exchanged within the different services of the hospital. Therefore, the use case does not explore the contents of the health information system, but it manages the concepts of cybersecurity and privacy risk assessment together with trust—which is achieved with a shareable, verifiable, unmodifiable log in the blockchain—and cyber hygiene—which are the set of strategies and associated measures in the form of human-centric controls for raising cybersecurity and data privacy awareness of different employee groups in healthcare organizations. For this aim, three validation scenarios in the use case approach have been planned for assessing different cybersecurity and privacy situations of interest, and are described in the following subsection.
Use case validation scenarios
In this work, three scenarios are defined in a fashion similar to Sindre and Opdahl[12] for the presented use case (and also accounting for misuse cases):
- “network configuration,” where the use case scenario is not threatened by cybersecurity nor privacy risks, in order to perform an assessment in a normal operation of the use case;
- “outpatient appointment check,” where the misuse case scenario is threatened by a denial-of-service attack, which prevents legitimate users from accessing internet services, including patient access to outpatient information; and
- “visualization of clinical information,” where the misuse case scenario proposes an inside URL attack to retrieve clinical information, causing a privacy risk.
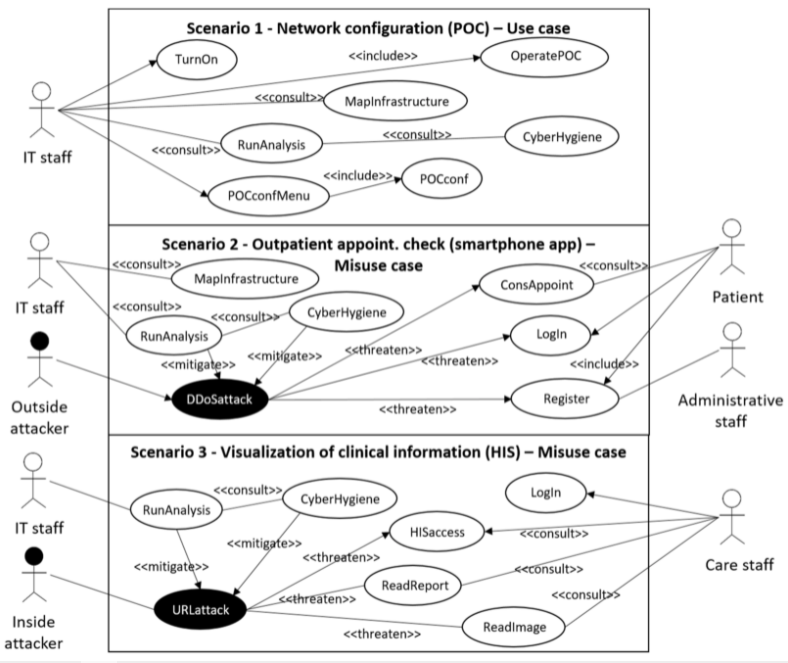
These three presented scenarios, which are focused on POC systems and dealing with cybersecurity and privacy risks in a healthcare setting, are depicted in Figure 2, and described below.
|
Scenario 1: Network configuration (POC): In this scenario, no cybersecurity attack nor information privacy leakage is simulated, but still new configurations to the IT infrastructure are simulated. In particular, it is simulated that the IT department has been requested to rearrange the IT infrastructure of the hospital, including medical devices, due to a health crisis situation, as occurred in 2020 due to the COVID-19 pandemic. For such a request, the IP/MAC address links of the medical devices pointing to the servers are modified. In this situation, the CUREX platform detects that the IP/MAC address links have been modified but no cybersecurity nor privacy risk has occurred. Therefore, the overall combined cybersecurity and privacy risk score obtained through the CUREX platform should be low.
Scenario 2: Outpatient appointment check (smartphone app): In this scenario, a distributed denial-of-service (DDOS) attack is simulated, which is considered high-risk for cybersecurity and low-risk for privacy. A participant is registered as a new simulated patient to access the simulated patient’s information through the test smartphone app, but a DDOS attack happens, resulting in the smartphone app functionality breaking down. Therefore, the participant is not able to access the information due to an out-of-service notice. In this situation, the CUREX platform has to provide a high score for cybersecurity risk and a low one for privacy risk; both values combined results in the overall value of a medium risk score reported by CUREX.
Scenario 3: Visualization of clinical information from the health information system: In this scenario, a URL-hacking cybersecurity attack with leakage of privacy information is simulated. The simulated scenario is that a participant, pretending to be a medical doctor, wants to have access to a medical image and a report of a simulated patient, but the participant intentionally accesses another patient’s data instead of the originally planned patient’s data. Therefore, the simulated cybersecurity attack also causes a privacy leakage of information, implying that both the cybersecurity and privacy information risks scores of the CUREX platform should be high.
In particular, it is of significant interest to at least pilot with Scenario 1 and either Scenario 2 or Scenario 3. Scenario 1 does not involve a cybersecurity attack but allows the CUREX toolkit to compute the cybersecurity and privacy risk when no attacks are detected. For Scenario 1, results should provide low risks to the organization and, therefore, they can continue sharing the data being requested. Conversely, the rationale behind Scenarios 2 and 3 involves simulating a cybersecurity attack and/or privacy leakage. The latter allows to assess the CUREX platform in terms of how scores change and analyze the quality of the suggested mitigation measures.
Develop technical infrastructure and CUREX tools
The technical developments for the use case proposed is a re-creation of part of the IT infrastructure of the hospital (also representative of many healthcare centers) in a pre-production environment. It is relevant that the infrastructure is developed in parallel since it is not possible to apply cybersecurity and privacy attacks and threats in a real infrastructure with real patient data and in-use equipment. Here resides one of the main points to apply use case approaches. In particular, as shown in Figure 3, the use case environment is firewall-disconnected, in any means of access, from the main infrastructure of the hospital. Therefore, the entire piloting environment is simulated but at the same time is highly representative of a real infrastructure. In particular, Figure 3a depicts the different entities composing the IT infrastructure, developed together while elucidating its logical connections to the different components. Moreover, Figure 3b shows the logical arrangement of virtual local area networks (VLANs) that consistently sectorize the different entities through the firewall hardware device. The logical arrangement consists of three VLANs, one for users to operate the workstations, another for the POC medical devices, and a third for the different servers and client applications to support the available services. Furthermore, the smartphone is connected to the use case environment through regular Wi-Fi or other internet access routes, although through a specific dedicated parallel connection channel to avoid any interference to the real infrastructure.
References
- ↑ Jalali, Mohammad S; Kaiser, Jessica P (28 May 2018). "Cybersecurity in Hospitals: A Systematic, Organizational Perspective" (in en). Journal of Medical Internet Research 20 (5): e10059. doi:10.2196/10059. ISSN 1438-8871. PMC PMC5996174. PMID 29807882. http://www.jmir.org/2018/5/e10059/.
- ↑ Jofre, M. (July 2020). "Holistic View Of Healthcare Cybersecurity Ecosystem". ResearchGate. doi:10.13140/RG.2.2.14306.96962. https://www.researchgate.net/publication/343722649_Holistic_View_Of_Healthcare_Cybersecurity_Ecosystem. Retrieved 21 July 2021.
- ↑ Tulasidas, Sivanesan; Mackay, Ruth; Hudson, Chris; Balachandran, Wamadeva (2017). "Security Framework for Managing Data Security within Point of Care Tests". Journal of Software Engineering and Applications 10 (02): 174–193. doi:10.4236/jsea.2017.102011. ISSN 1945-3116. http://www.scirp.org/journal/doi.aspx?DOI=10.4236/jsea.2017.102011.
- ↑ Williams, Patricia; Woodward, Andrew (1 July 2015). "Cybersecurity vulnerabilities in medical devices: a complex environment and multifaceted problem" (in en). Medical Devices: Evidence and Research 8: 305-316. doi:10.2147/MDER.S50048. ISSN 1179-1470. PMC PMC4516335. PMID 26229513. http://www.dovepress.com/cybersecurity-vulnerabilities-in-medical-devices-a-complex-environment-peer-reviewed-article-MDER.
- ↑ Reason, J. (18 March 2000). "Human error: models and management". BMJ 320 (7237): 768–770. doi:10.1136/bmj.320.7237.768. PMC PMC1117770. PMID 10720363. https://www.bmj.com/lookup/doi/10.1136/bmj.320.7237.768.
- ↑ 6.0 6.1 Sardi, Alberto; Rizzi, Alessandro; Sorano, Enrico; Guerrieri, Anna (27 August 2020). "Cyber Risk in Health Facilities: A Systematic Literature Review" (in en). Sustainability 12 (17): 7002. doi:10.3390/su12177002. ISSN 2071-1050. https://www.mdpi.com/2071-1050/12/17/7002.
- ↑ 7.0 7.1 Wagner, Isabel; Boiten, Eerke (2018), Garcia-Alfaro, Joaquin; Herrera-Joancomartí, Jordi; Livraga, Giovanni et al.., eds., "Privacy Risk Assessment: From Art to Science, by Metrics" (in en), Data Privacy Management, Cryptocurrencies and Blockchain Technology (Cham: Springer International Publishing) 11025: 225–241, doi:10.1007/978-3-030-00305-0_17, ISBN 978-3-030-00304-3, http://link.springer.com/10.1007/978-3-030-00305-0_17
- ↑ Hameed, Shilan S.; Hassan, Wan Haslina; Latiff, Liza Abdul; Ghabban, Fahad (23 March 2021). "A systematic review of security and privacy issues in the internet of medical things; the role of machine learning approaches" (in en). PeerJ Computer Science 7: e414. doi:10.7717/peerj-cs.414. ISSN 2376-5992. PMC PMC8022640. PMID 33834100. https://peerj.com/articles/cs-414.
- ↑ Coronado, Anthony J.; Wong, Timothy L. (1 January 2014). "Healthcare Cybersecurity Risk Management: Keys To an Effective Plan". Biomedical Instrumentation & Technology 48 (s1): 26–30. doi:10.2345/0899-8205-48.s1.26. ISSN 0899-8205. https://doi.org/10.2345/0899-8205-48.s1.26.
- ↑ Kandasamy, Kamalanathan; Srinivas, Sethuraman; Achuthan, Krishnashree; Rangan, Venkat P. (26 May 2020). "IoT cyber risk: a holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process". EURASIP Journal on Information Security 2020 (1): 8. doi:10.1186/s13635-020-00111-0. ISSN 2510-523X. https://doi.org/10.1186/s13635-020-00111-0.
- ↑ Larman, Craig. Applying UML and patterns: an introduction to object-oriented analysis and design and iterative development (3rd ed ed.). Upper Saddle River, N.J: Prentice Hall PTR, c2005. ISBN 978-0-13-148906-6.
- ↑ 12.0 12.1 12.2 12.3 Sindre, Guttorm; Opdahl, Andreas L. (24 June 2004). "Eliciting security requirements with misuse cases" (in en). Requirements Engineering 10 (1): 34–44. doi:10.1007/s00766-004-0194-4. ISSN 0947-3602. https://doi.org/10.1007/s00766-004-0194-4.
- ↑ Cockburn, Alistair (2001). Writing effective use cases. The Crystal series for software development. Boston: Addison-Wesley. ISBN 978-0-201-70225-5.
- ↑ Constantine, L.L.; Lockwood, L.A.D. (1999). Software for Use: A Practical Guide to the Models and Methods of Usage-Centered Design (1st ed.). Addison-Wesley. ISBN 9780768685305.
- ↑ Jacobson, Ivar (1992). Object-oriented software engineering: a use case driven approach. [New York] : Wokingham, Eng. ; Reading, Mass: ACM Press ; Addison-Wesley Pub. ISBN 978-0-201-54435-0.
- ↑ Yue, Tao; Briand, Lionel C.; Labiche, Yvan (4 March 2013). "Facilitating the transition from use case models to analysis models: Approach and experiments". ACM Transactions on Software Engineering and Methodology 22 (1): 5:1–5:38. doi:10.1145/2430536.2430539. ISSN 1049-331X. https://doi.org/10.1145/2430536.2430539.
- ↑ "CUREX". University of Piraeus Research Center. 2020. https://curex-project.eu/. Retrieved 26 April 2021.
- ↑ Diaz-Honrubia, Antonio Jesus; Rodriguez Gonzalez, Alejandro; Mora Zamorano, Juan; Rey Jiménez, Jesús; Gonzalez-Granadillo, Gustavo; Diaz, Rodrigo; Konidi, Mariza; Papachristou, Panos et al. (1 June 2019). "An Overview of the CUREX Platform". 2019 IEEE 32nd International Symposium on Computer-Based Medical Systems (CBMS): 162–167. doi:10.1109/CBMS.2019.00042. https://ieeexplore.ieee.org/document/8787402/.
- ↑ Mohammadi, Farnaz; Panou, Angeliki; Ntantogian, Christoforos; Karapistoli, Eirini; Panaousis, Emmanouil; Xenakis, Christos (14 October 2019). "CUREX: seCUre and pRivate hEalth data eXchange". IEEE/WIC/ACM International Conference on Web Intelligence - Companion Volume. WI '19 Companion (Thessaloniki, Greece: Association for Computing Machinery): 263–268. doi:10.1145/3358695.3361753. ISBN 978-1-4503-6988-6. https://doi.org/10.1145/3358695.3361753.
- ↑ Panda, Sakshyam; Panaousis, Emmanouil; Loukas, George; Laoudias, Christos (11 January 2020). "Optimizing Investments in Cyber Hygiene for Protecting Healthcare Users". arXiv. arXiv:2001.03782v1. http://arxiv.org/abs/2001.03782.
- ↑ Jofre, M. (June 2020). "Minimum quality standard for cybersecurity training in healthcare – SecureHospitals.eu". ResearchGate. doi:10.13140/RG.2.2.17662.41289. https://www.researchgate.net/publication/343722644_Minimum_quality_standard_for_cybersecurity_training_in_healthcare_-_SecureHospitalseu. Retrieved 21 July 2021.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added.