Difference between revisions of "Main Page/Featured article of the week/2022"
Shawndouglas (talk | contribs) (Added last week's article of the week) |
Shawndouglas (talk | contribs) (Added last week's article of the week) |
||
| Line 17: | Line 17: | ||
<!-- Below this line begin pasting previous news --> | <!-- Below this line begin pasting previous news --> | ||
<h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 24–30:</h2> | <h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 31–February 06:</h2> | ||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig3 Chong ITMWebConf21 36.png|240px]]</div> | |||
'''"[[Journal:Privacy-preserving healthcare informatics: A review|Privacy-preserving healthcare informatics: A review]]"''' | |||
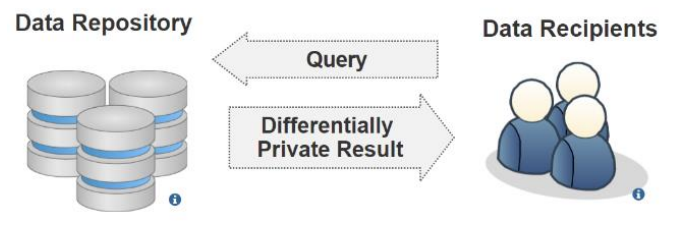
The [[electronic health record]] (EHR) is the key to an efficient healthcare service delivery system. The publication of healthcare data is highly beneficial to healthcare industries and government institutions to support a variety of medical and census research. However, healthcare data contains sensitive [[information]] of patients, and the publication of such data could lead to unintended [[Information privacy|privacy]] disclosures. In this paper, we present a comprehensive survey of the state-of-the-art privacy-enhancing methods that ensure a secure healthcare [[data sharing]] environment. We focus on the recently proposed schemes based on data anonymization and differential privacy approaches in the protection of healthcare data privacy. We highlight the strengths and limitations of the two approaches and discuss some promising future research directions in this area. ('''[[Journal:Privacy-preserving healthcare informatics: A review|Full article...]]''')<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 24–30:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig5 Jebali JofInfoTelec2020 5-1.jpg|240px]]</div> | <div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig5 Jebali JofInfoTelec2020 5-1.jpg|240px]]</div> | ||
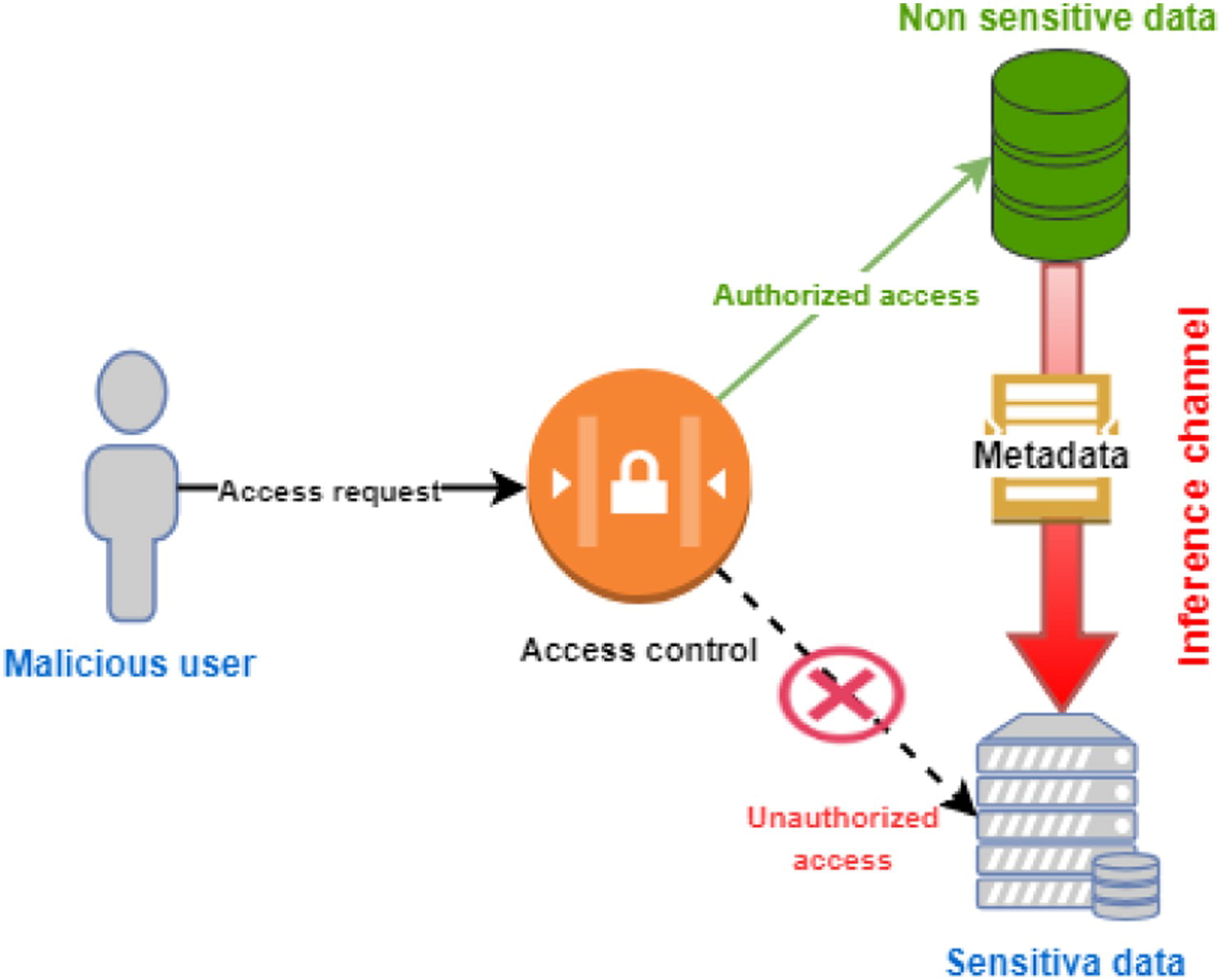
'''"[[Journal:Secure data outsourcing in presence of the inference problem: Issues and directions|Secure data outsourcing in presence of the inference problem: Issues and directions]]"''' | '''"[[Journal:Secure data outsourcing in presence of the inference problem: Issues and directions|Secure data outsourcing in presence of the inference problem: Issues and directions]]"''' | ||
Revision as of 15:43, 7 February 2022
|
|
If you're looking for other "Article of the Week" archives: 2014 - 2015 - 2016 - 2017 - 2018 - 2019 - 2020 - 2021 - 2022 |
Featured article of the week archive - 2022
Welcome to the LIMSwiki 2022 archive for the Featured Article of the Week.
Featured article of the week: January 31–February 06:"Privacy-preserving healthcare informatics: A review" The electronic health record (EHR) is the key to an efficient healthcare service delivery system. The publication of healthcare data is highly beneficial to healthcare industries and government institutions to support a variety of medical and census research. However, healthcare data contains sensitive information of patients, and the publication of such data could lead to unintended privacy disclosures. In this paper, we present a comprehensive survey of the state-of-the-art privacy-enhancing methods that ensure a secure healthcare data sharing environment. We focus on the recently proposed schemes based on data anonymization and differential privacy approaches in the protection of healthcare data privacy. We highlight the strengths and limitations of the two approaches and discuss some promising future research directions in this area. (Full article...)
|