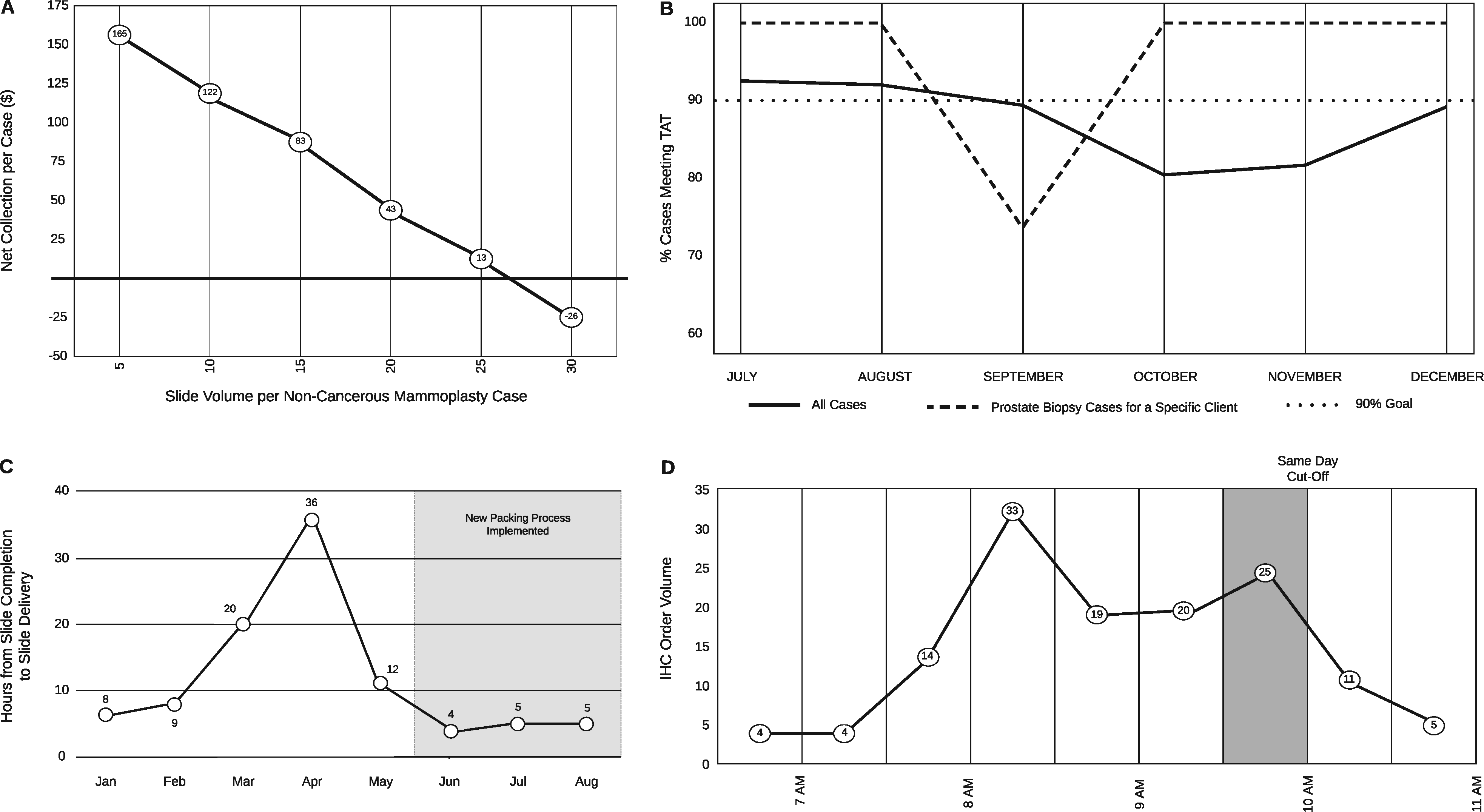
Featured article of the week: February 14–20:"Informatics-driven quality improvement in the modern histology lab"
Laboratory information systems (LISs) and data visualization techniques have untapped potential in anatomic pathology laboratories. The pre-built functionalities of an LIS do not address all the needs of a modern histology laboratory. For instance, “go live” is not the end of LIS customization, only the beginning. After closely evaluating various histology lab workflows, we implemented several custom data analytics dashboards and additional LIS functionalities to monitor and address weaknesses. Herein, we present our experience with LIS and data-tracking solutions that improved trainee education, slide logistics, staffing and instrumentation lobbying, and task tracking. The latter was addressed through the creation of a novel “status board” akin to those seen in inpatient wards. These use-cases can benefit other histology laboratories. (Full article...)
Featured article of the week: February 07–13:
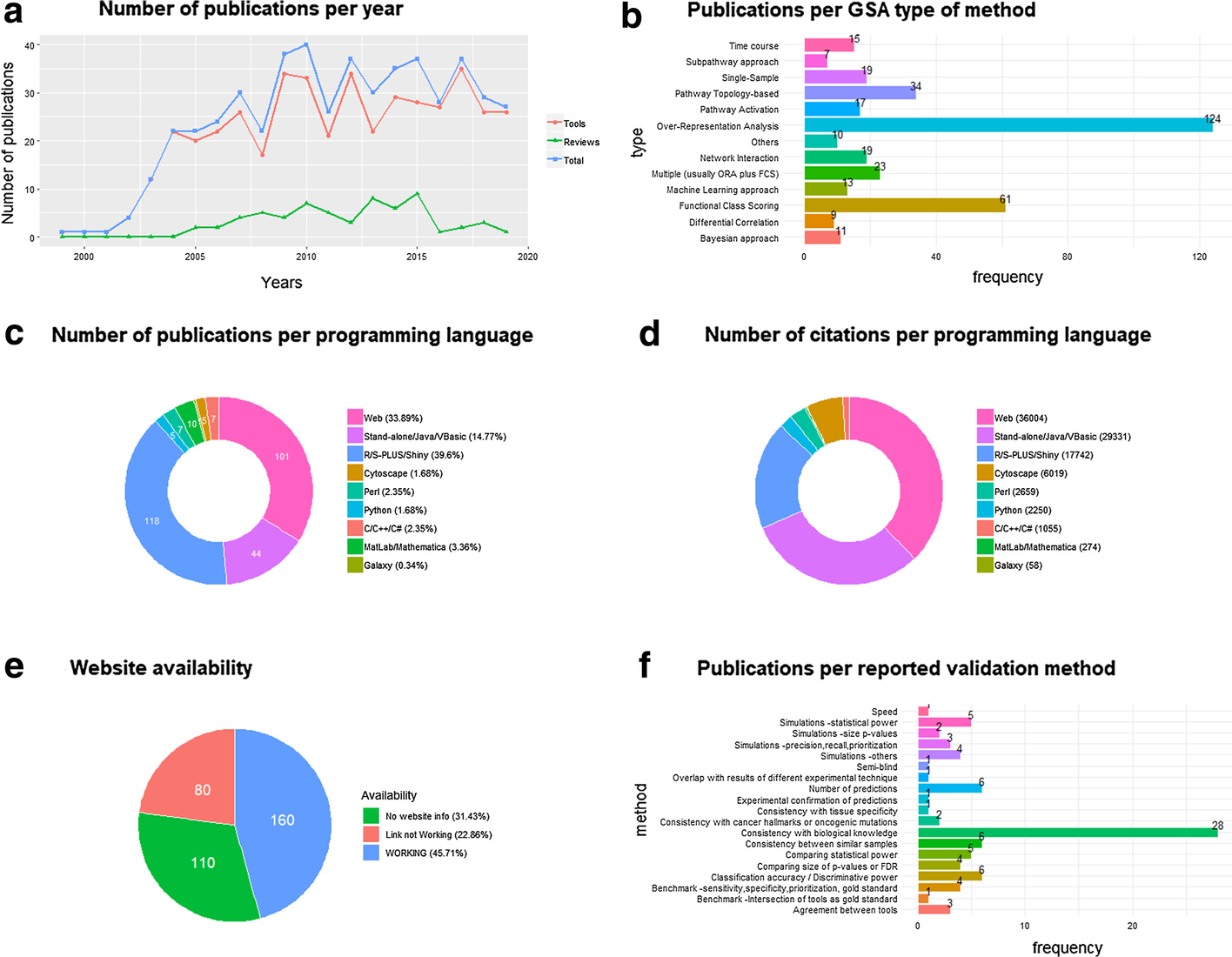
"Popularity and performance of bioinformatics software: The case of gene set analysis"
Gene set analysis (GSA) is arguably the method of choice for the functional interpretation of omics results. This work explores the popularity and the performance of all the GSA methodologies and software published during the 20 years since its inception. "Popularity" is estimated according to each paper's citation counts, while "performance" is based on a comprehensive evaluation of the validation strategies used by papers in the field, as well as the consolidated results from the existing benchmark studies. Regarding popularity, data is collected into an online open database ("GSARefDB") which allows browsing bibliographic and method-descriptive information from 503 GSA paper references; regarding performance, we introduce a repository of Jupyter Notebook workflows and Shiny apps for automated benchmarking of GSA methods (“GSA-BenchmarKING”). After comparing popularity versus performance, results show discrepancies between the most popular and the best performing GSA methods. (Full article...)
|
Featured article of the week: January 31–February 06:
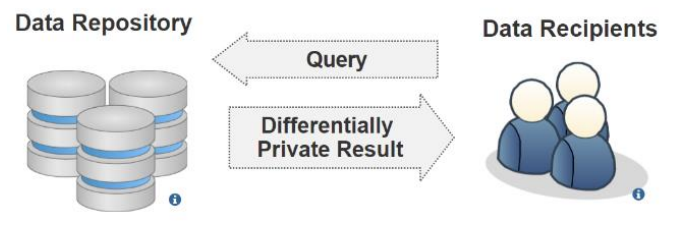
"Privacy-preserving healthcare informatics: A review"
The electronic health record (EHR) is the key to an efficient healthcare service delivery system. The publication of healthcare data is highly beneficial to healthcare industries and government institutions to support a variety of medical and census research. However, healthcare data contains sensitive information of patients, and the publication of such data could lead to unintended privacy disclosures. In this paper, we present a comprehensive survey of the state-of-the-art privacy-enhancing methods that ensure a secure healthcare data sharing environment. We focus on the recently proposed schemes based on data anonymization and differential privacy approaches in the protection of healthcare data privacy. We highlight the strengths and limitations of the two approaches and discuss some promising future research directions in this area. (Full article...)
|
Featured article of the week: January 24–30:
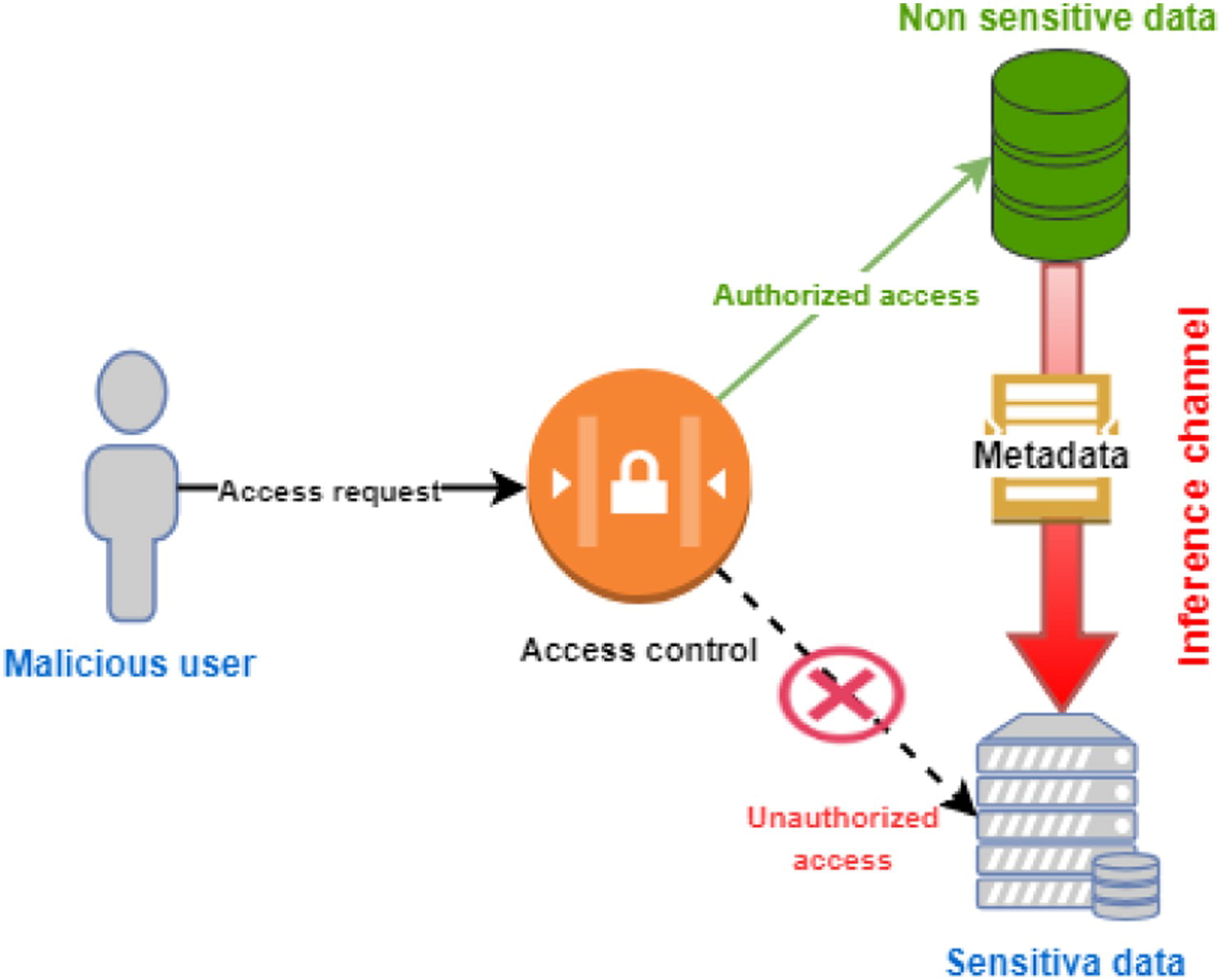
"Secure data outsourcing in presence of the inference problem: Issues and directions"
With the emergence of the cloud computing paradigms, secure data outsourcing—moving some or most data to a third-party provider of secure data management services—has become one of the crucial challenges of modern computing. Data owners place their data among cloud service providers (CSPs) in order to increase flexibility, optimize storage, enhance data manipulation, and decrease processing time. Nevertheless, from a security point of view, access control proves to be a major concern in this situation seeing that the security policy of the data owner must be preserved when data is moved to the cloud. The lack of a comprehensive and systematic review on this topic in the available literature motivated us to review this research problem. Here, we discuss current and emerging research on privacy and confidentiality concerns in cloud-based data outsourcing and pinpoint potential issues that are still unresolved. (Full article...)
|
Featured article of the week: January 17–23:
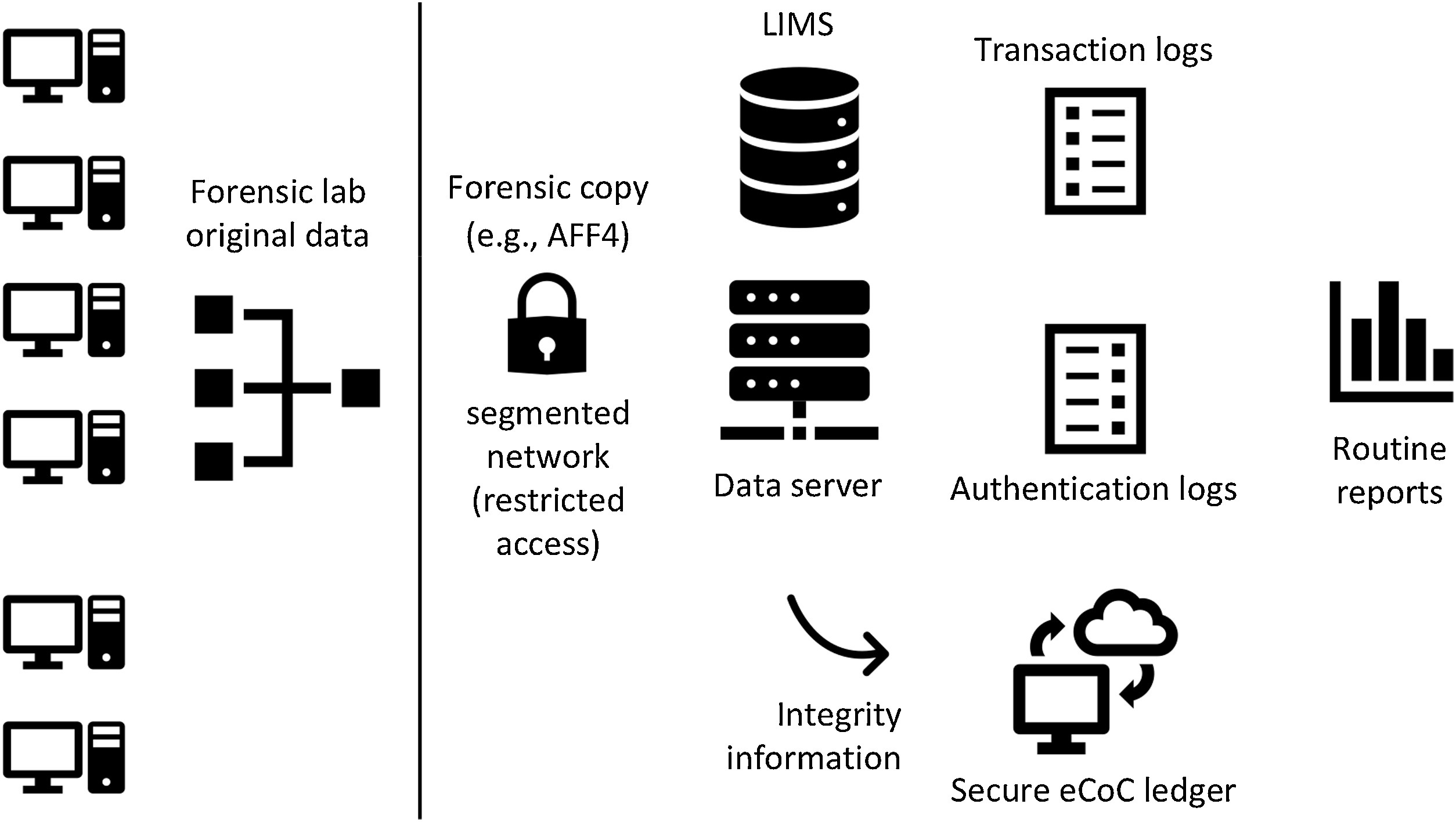
"Digital transformation risk management in forensic science laboratories"
Technological advances are changing how forensic laboratories operate in all forensic disciplines, not only digital. Computers support workflow management and enable evidence analysis (physical and digital), while new technology enables previously unavailable forensic capabilities. Used properly, the integration of digital systems supports greater efficiency and reproducibility, and drives digital transformation of forensic laboratories. However, without the necessary preparations, these digital transformations can undermine the core principles and processes of forensic laboratories. Forensic preparedness concentrating on digital data reduces the cost and operational disruption of responding to various kinds of problems, including misplaced exhibits, allegations of employee misconduct, disclosure requirements, and information security breaches ... (Full article...)
|
Featured article of the week: January 10–16:
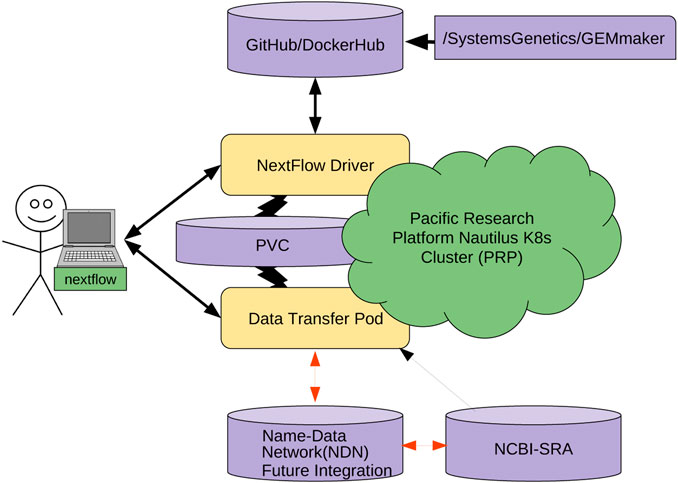
"Named data networking for genomics data management and integrated workflows"
Advanced imaging and DNA sequencing technologies now enable the diverse biology community to routinely generate and analyze terabytes of high-resolution biological data. The community is rapidly heading toward the petascale in single-investigator laboratory settings. As evidence, the National Center for Biotechnology Information (NCBI) Sequence Read Archive (SRA) central DNA sequence repository alone contains over 45 petabytes of biological data. Given the geometric growth of this and other genomics repositories, an exabyte of mineable biological data is imminent. The challenges of effectively utilizing these datasets are enormous, as they are not only large in size but also stored in various geographically distributed repositories such as those hosted by the NCBI, as well as in the DNA Data Bank of Japan (DDBJ), European Bioinformatics Institute (EBI), and NASA’s GeneLab. (Full article...)
|
Featured article of the week: January 3–9:
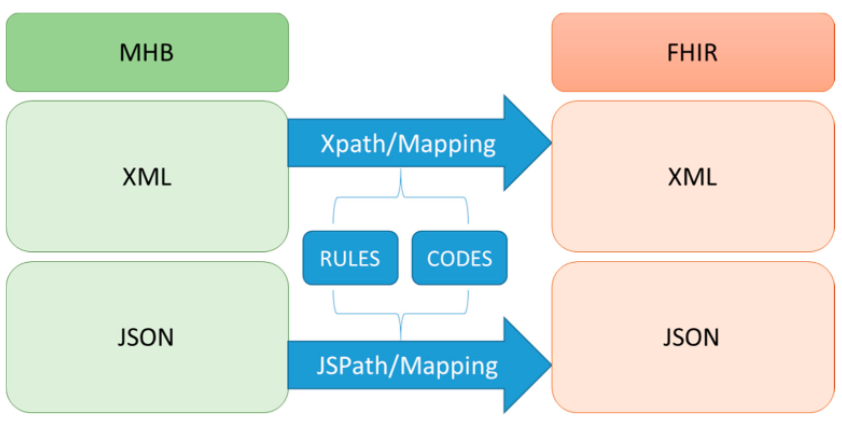
"Implement an international interoperable PHR by FHIR: A Taiwan innovative application"
Personal health records (PHRs) have many benefits for things such as health surveillance, epidemiological surveillance, self-control, links to various services, public health and health management, and international surveillance. The implementation of an international standard for interoperability is essential to accessing PHRs. In Taiwan, the nationwide exchange platform for electronic medical records (EMRs) has been in use for many years. The Health Level Seven International (HL7) Clinical Document Architecture (CDA) was used as the standard for those EMRs. However, the complication of implementing CDA became a barrier for many hospitals to realizing standard EMRs. In this study, we implemented a Fast Healthcare Interoperability Resources (FHIR)-based PHR transformation process, including a user interface module to review the contents of PHRs. (Full article...)
|
|